These days, a business’s network going down can spell massive losses. Since most businesses deal at least somewhat with digital goods or at least rely on their websites to gather customers, the shutdown of a business’ network can mean large device disruptions and even monetary losses.
Because of this, businesses have flocked to invest in the security of their networks. From firewalls to dedicated network management software. None of these can function properly if you don’t have a good view of your entire network. Because of this, network monitoring has become a crucial part of business management.
What Is Network Monitoring?
Network monitoring is a subset of network management dealing with identifying failing or lacking components within your network, ideally before they cause any issues. Frequent freezes, crashes, server overloads, or failed switches are common symptoms of an unmonitored network. Network monitoring deals with looking at a variety of different metrics to determine whether there’s an issue in the network. If a malfunction happens, the network monitoring system should inform the Administrator immediately so that they can fix it.
In the 21st century, networks are extremely complex, and monitoring them by hand has become somewhat of Herculean labor. Because of this, most administrators will rely on their network monitoring tool of choice to manage a network. These tools allow the admin to track network performance and figure out what issues and bottlenecks might arise. Some more advanced tools will also perform root-cause analysis to make troubleshooting easier, or make resource utilization prognoses to ensure your network never faces resource troubles.
How Do You Use A Network Traffic Monitor?
The first thing you need to make clear for your network monitoring efforts to pay off is to identify what devices need to be monitored, as well as their performance metrics. Afterward, you should choose a monitoring interval that suits what you’re monitoring.
An example of this is routers and servers. These perform crucial functions in a business ecosystem, a server failure can mean weeks of trouble for a business, so they need to be monitored frequently. So, that means you should prioritize monitoring efforts based on how crucial the network component is to your operations. Ideally, the tool you’re using should allow you to set up alerts in a way that you don’t get an alert if an employee’s PC is running a bit slow, but you get it before critical server failure.
A network monitoring plan needs to think about every aspect of your IT infrastructure. You should have a unified view of the network as a whole and have your tool update it in real-time. This lets your administrators focus on keeping the network running smoothly, rather than constantly checking for updates.
If you’ve got a web traffic monitor, it should be reported to your IT team constantly. A quality tool will give you basic drill-down and reporting capabilities to quickly get people on board in case an issue occurs.
Why You Should Monitor Network Devices
Monitoring each network device is crucial in ensuring that the device is available and working when you need it. All devices can fail, regardless of how rugged or simple they are. Generally, you’ll see device availability be expressed as the percentage of time the device runs without a hitch. Now, for some devices, it might not be the end of the world if they fail. However, some devices will cause the whole network to clog up, or even go down in case they fail. Enough routers doing a sub-par job is enough to clog up a network by itself. Because of this, your network monitoring tool must cover all of the devices on your network.
What Are The Most Common Network Devices?
- Routers Used to link networks together. One of the most common uses is connecting an in-house network to the internet. A router’s job is to find the best path for data to take in your network. Routers are Layer 3 devices.
- Switches Simple devices connecting computers, servers, printers, and other devices to your private network. Its job is simply to allow different devices to communicate with each other. Switches operate in the 2nd layer.
- Firewalls One of the most common cybersecurity tools installed on networks. A firewall’s job is to set rules that will govern traffic that comes into and goes out of your network.
- Servers Arguably the most important devices on networks. This is where apps and large data reside. Servers are used to accept requests from users and give appropriate responses.
What Are Network Device Monitoring Task Boundaries?
Unfortunately, the network monitoring software market is pretty much divided into two different kinds of monitoring tools. These are network performance monitoring packages and traffic analyzers.
Fundamentally, these are two different tasks, even if they’re done by the same tool. The first of these tasks is simply looking after the devices and ensuring they’re working properly and have enough capacity for the load you’re putting them under. The second is to look over traffic flows within your system and ensure everything is in proper order. Because of this, when purchasing a tool for network device monitoring, make sure it’s a network performance monitor with a device focus, rather than a traffic analyzer.
What Network Device Documentation Do I Need?
The most essential information you need to have about your network is the numbers and types of each network device. Next, you should know the name, model, firmware name, version, and age of each device. This is information that goes into your network asset inventory, and some popular tools like the SolarWinds Network Monitor will automate this.
Next, you’ll need to document the layout of your network, this process is called network mapping. This means creating a list of all the ports on every switch and router as well as what devices are plugged into the other side.
You need both the network topology map and network asset inventory to properly monitor a network. While this can be done manually in some smaller businesses, there are free tools out there that’ll automate the process such as Nagios Core.
Managing Network Devices
All of the data you’ve collected into your network asset inventory will also contain unique identifiers for each of your devices, such as their IP and MAC addresses. Since most networks don’t deal with static IP addresses, this info lets you get into operational data. You can link that catalog to an IP address manager from there.
Chances are you’re already running a DHCP server for IP allocation and a DNS server for hostname referencing. However, if you’re not, that’s a relatively common cause of random network errors.
An IP manager works in coordination with both your DHCP and DNS server to ensure every IP allocated is also accounted for, in addition to solving a myriad of common issues like addressing duplication and abandonment. The combo of DNS, DHCP, and IP address managers is referred to as DDI.
Once you’ve got an asset inventory sorted out, you can start standardizing all of your device settings. Usually, businesses use a network configuration manager to implement this. To avoid security flaws you’ll need to ensure that all of these devices have their firmware updated whenever there’s a patch available. While this can be done manually, it’s much easier to let a patch manager handle the whole process.
Because of this, centralized monitoring approaches naturally lead to network management tools. This means that to have the easiest time managing your network, you’ll need:
- A network configuration manager
- A DDI tool
- A patch management solution
While this might seem like a lot at first, these tools will save a lot of time by automating tedious tasks. They’ll prevent network errors, breakdowns, and security flaw exploitation from happening to your network. Since all of these tools make a log of their findings, you can use that as an audit trail for data privacy standard compliance.
Live Network Device Monitoring
Now, when most people think of network device monitoring, what they’re thinking of is live issue tracking. This means looking at the statuses of switches and routers within the network to ensure that they’re performing at optimum capacity. This means looking at metrics like CPU, memory utilization, and capacity, as well as the throughput of each port.
This is the part of network device monitoring where a tool stops being optional. These things are simply way too difficult to monitor manually in any network spanning more than a couple of devices.
Network device monitoring solutions will provide you with a dashboard where you and your IT team can see network device details in real-time. You can also set up alerts so that if certain thresholds are met or exceeded, you’ll be immediately notified. This way, if a problem occurs, you’ll be able to get right to troubleshooting.
This is also great because you don’t need to have someone employed to watch a dashboard all day, since you’ll get a notification if anything goes wrong. With some tools, you can set it up so that you’re alerted if the tool suspects something will go wrong soon. Once you’re alerted, you can allocate staff to fixing the issue.
Network performance monitors also collect throughput statistics, which helps them set up default thresholds. This lets you get alerted in case the tool anticipates your capacity will be exceeded soon, letting you stop problems before they even happen. This is especially crucial for video conferencing, VoIP, or similar applications’ performance.
What Is SNMP?
SNMP is the Simple Network Management Protocol. It’s the best way to monitor network devices available. It is also a reporting standard, including a format for a standard report, as well as procedures you should follow to get that report from each device on your network.
In the reporting system, there are two main actors: the SNMP Device Agent and the SNMP Manager. Since the SNMP system has worked so well so far, pretty much every network device producer installs an SNMP agent for each of their devices. However, on many of these, it’ll be turned off by default. This means the deployment aspect of SNMP is usually as simple as turning all of these on. However, you still need an SNMP Manager. Thankfully, most network performance monitors can perform the role of an SNMP Manager.
SNMP’s most common reporting format is referred to as MIB or Management Information Base. The MIB is a text-only layout that has a code for each reporting value, forming a tree when it’s dereferenced. SNMP agents constantly scan the devices they’re on searching for issues.
SNMP reporting is a process that starts when the SNMP Manager sends a request. Since its request is broadcast in an area, the Manager doesn’t need to know any of the devices on the network itself. The SNMP Agent is running on a network device, meaning all broadcast traffic will get to it, this leads to the agent sending its MIB to the Manager. When this is done, data from the MIB is shown as live activity in a monitor’s console.
MIB is responsible for the autodiscovery function most network performance monitoring tools these days are equipped with. The MIB contains enough information to craft an asset inventory together with a network topology map.
Since the manager is always sending out requests, and the agent is always responding, the data you see on the console or dashboard is always in real-time. Alerts systems function similarly, with agents sending out a MIB by themselves in case they detect a high-severity issue.
An SNMP-based network monitoring system
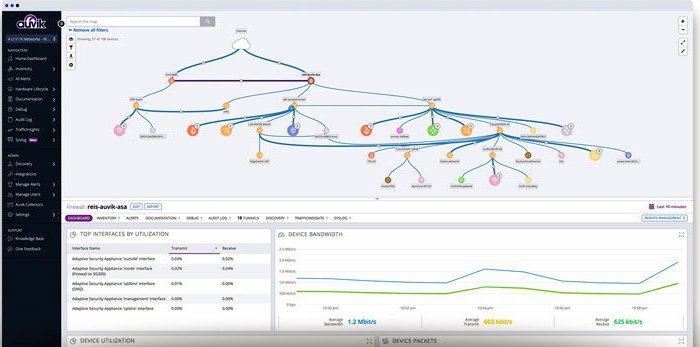
Auvik – FREE TRIAL
The easiest way to understand how a system works is to look at an example. Auvik is a cloud-based network monitoring package that creates an SNMP Manager by downloading a program onto a server that is connected to the monitored network. Following the protocol, the SNMP manager requests and receives MIBs. It uploads them to the Auvik cloud server.
Auvik extracts device information, such as make, model, year, and capacity. This gets compiled into a hardware inventory. Each MIB includes details of every interface on the monitored device and the device that it connects to. This information enables Auvik to generate a network topology map.
Finally, Auvik uses status information in the MIB for its network device monitoring console. If the collector receives an SNMP Trap, that is uploaded and Auvik displays it in the network monitoring console as an alert. It won’t cost you anything to download Auvik just to examine how SNMP works because it is available for a 14-day free trial.
Closing Words
As you can see, network device monitoring is quite a complex process. Thankfully, it is greatly simplified through the use of SNMP and a network device monitoring tool. Some of these tools can automate pretty much everything you’ve read about in this article, leaving your technicians to focus on more complex tasks.
Since most business networks are connected to the internet, you can even use an SNMP forwarder from a remote site, and centralize all of your monitoring efforts in one location. This is what makes cloud monitoring tools feasible.
All in all, we recommend getting a network monitoring tool to automate the tedious parts of network device monitoring and ensure maximum uptime.