You may have already heard the buzz around Simjacker.
Basically, attackers found some vulnerabilities in the authentication and proprietary security mechanisms implemented by dynamic SIM tool-kits embedded in modern SIM cards.
A wide range of SIM cards have been remotely exploited causing hacks into mobile phones simply by sending a specially crafted binary SMS.
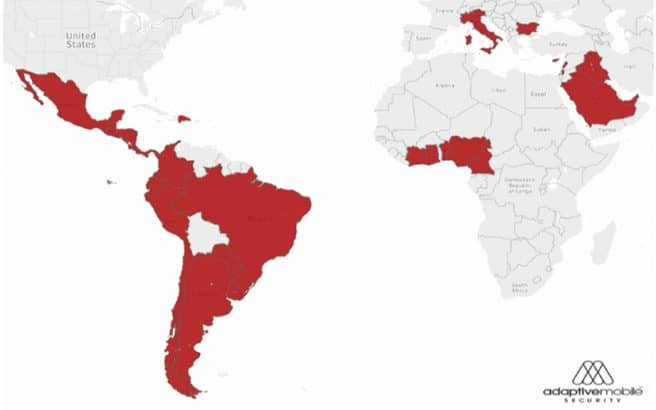
According to a report by Cybersecurity researchers at Adaptive Mobile, there are 29 affected countries across five continents:
- North America: Mexico, Guatemala, Honduras, Costa Rica, Nicaragua, Belize, El Salvador, Dominican Republic, and Panama
- South America: Peru, Colombia, Brazil, Ecuador, Chile, Argentina, Uruguay, and Paraguay
- Europe: Italy, Bulgaria, and Cyprus
- Africa: Nigeria, Ghana, Benin, Ivory Coast, and Cameroon
- Asia: Saudi Arabia, Iraq, Palestine and Lebanon
61 mobile operators are actively using vulnerable SIMs with S@T Browser toolkits.
According to researchers, “the most probable, conservative estimate is that mid to high hundreds of millions of SIM Cards globally are effected.”
How it Works:
Simjacker involves a SMS containing a specific type of spyware-like code being sent to a mobile phone.
This code instructs the IUCC (SIM Card) within the phone to “take over” the mobile phone, in order to retrieve and perform sensitive commands.
The attack exploits SIM cards that come with a pre-installed Java applet named the S@T Browser.
During the attack, the user is completely unaware that they received the SMS with the Simjacker Attack message, that information was retrieved, and that it was sent outwards in the Data Message SMS – there is no indication in any SMS inbox or outbox.
Basically, simjacker hijacks your phone number to gain access to other accounts or information linked to this number.
For example, you may have setup two-factor authentication for logging into your bank account.
To reset your bank password, perhaps you have a code sent to your phone number.
If Simjacker hijacks your phone number and uses it to gain access to your accounts, the verification code will be sent to them, and you wouldn’t even know.
That is just one example of how Simjacker can take over the mobile phone and use it to cause harm.
Not only can Simjacker hijack your phone number, it retrieves the persons locations, and can also perform other commands such as:
- Play Tone
- Send Short Message
- Set Up Call
- Send USSD
- Send SS
- Provide Local Information: Location information, IMEI, Battery, Network, Language, etc.
- Send DTMP Command
- Launch Browser
Simjacker attacks in Mexico, Colombia, and Peru:
Although this vulnerability has been around for a while, in September 2019, Adaptive Mobile said the attacks had been used in the real world.
At the Virus Bulletin 2019 security conference, the list of the 29 vulnerable countries was revealed along with countries where actual attacks were detected.
These countries included Mexico, Colombia, and Peru.
As far as they can tell, Adaptive Mobile says Simjacker attacks had only been used to track users’ locations and nothing more.
They also believe to have found evidence that Simjacker was developed by an unnamed company that sells surveillance software to governments across the world.
In a blog post published by Adaptive Mobile, “We have not named the specific company that we believe is responsible, as to do so, we would need to release some additional proof, that proof would also reveal specific methods and information that would impact our ability to protect subscribers.”
How to Protect Yourself:
Unfortunately, there is no guaranteed way to protect yourself from a Simjacker attack or for a mobile subscriber to even know whether a SIM Browser Toolkit is deployed on their SIM card or not.
There are apps available, such as SnoopSnitch, that will detect attacks based on suspicious binary SMS, but even knowing that won’t necessarily help you or protect you.
The only thing we can all do at this point in time is wait for our mobile operators to implement security measures or migrate our phone numbers to safer networks, thus providing new SIM cards.
But for those who need assurances, SRLabs updated its SIMTester app last month to support Simjacker scans.
The app will be able to tell users if they have the S@T Browser app installed on their SIM card, and if the app has been misconfigured and left vulnerable to Simjacker attacks.