It has been confirmed that earlier this week AWS was bit by a sustained DDoS attack.
The attack appears to have lasted around eight hours, hitting its Route 53 web offering and taking down other services.
The nature of the attack raises questions about AWS’s own mitigation service “Shield Advanced.”
Around the same time, Google Cloud Platform (GCP) reported interruptions to “multiple Cloud products including Google Compute Engine, Cloud Memorystore, Google Kubernetes Engine, Cloud Bigtable, and Google Cloud Storage.”
They claim that even though these disruptions were around the same time as the DDoS attack on AWS, they are not attributed to a malicious attack.
According to a Google Spokesperson, “The DDoS attack that impacted AWS services did not affect Google Cloud Services.”
AWS DDoS Attack
Although AWS described the impact of the attack as only affecting “a small number of specific DNS names,” the US East Coast seems to have been hit harder than other parts of the world with many customers unable to access AWS’s S3 services.
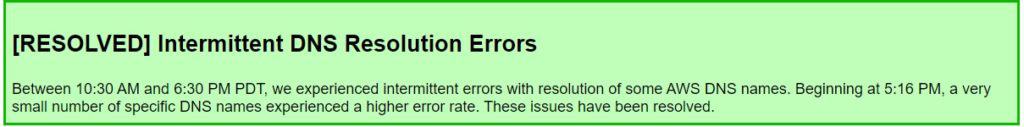
An AWS update claims that “Between 10:30 AM and 6:30 PM PDT, we experienced intermittent errors with resolution of some AWS DNS names. Beginning at 5:16 PM, a very small number of specific DNS names experienced a higher error rate. These issues have been resolved.”
Many of AWS’s services rely on DNS queries including their Relational Database Service and Elastic Load Balancing.
AWS sent an email to customers informing them of a Distributed Denial of Service (DDoS) attack.
According to The Register, email notes include: “We are investigating reports of occasional DNS resolution errors. The AWS DNS servers are currently under a DDoS attack.”
Furthermore, the email stated that “Our DDoS mitigations are absorbing the vast majority of this traffic, but these mitigations are also flagging some legitimate customer queries at this time. We are actively working on additional mitigations, as well as tracking down the source of the attack to shut it down.”
Given the large size of AWS and the traffic it handles, the attack must have been pretty significant.
AWS has not commented or answered anymore questions about the attack at this time.