With today’s businesses expanding their digital footprint more and more, digital risks grow in kind. Every new device, cloud service, or remote network connection increases your “attack surface”.
An attack surface is a very broad term, is defined as the sum of all endpoints from which an unauthorized entity can gain access to your system to enter or extract data. Every time you add another endpoint, you’re increasing your attack surface. With this comes the increasing complexity of what you need to do to properly protect it.
Here is our list of the best attack surface monitoring tools:
- Intruder – EDITOR’S CHOICE This attack surface scanner offers three plan levels that range from a monthly scan to a continuous service that allows for on-demand scanning as well. It covers premises and cloud services and is available for a 14-day free trial.
- ManageEngine Vulnerability Manager Plus – FREE TRIAL A comprehensive attack surface monitoring tool covering vulnerability discovery, severity, and remediation. Start a 30-day free trial.
- Rapid7 InsightVM Although not a dedicated ASM tool, the Rapid7 InsightVM offers most of the features provided by the top attack surface monitors in addition to its vulnerability management capabilities. It features excellent third-party risk assessment features, is entirely cloud-based, easily scalable, and provides timely alerts. All of these features are wrapped up in a modern, intuitive GUI. The tool offers a month-long free trial.
- FireCompass Attack Surface Management Platform A newer ASM that has been showing a lot of promise with its extremely focused approach targeted towards medium and large businesses.
- Bugcrowd Asset Inventory Created by white hat hackers, this crawler does a great job of supporting any attack surface monitoring strategy.
- Digital Shadows SearchLight An extremely innovative tool capable of alerting you of imminent attacks.
- OWASP Zed Attack Proxy The best free and open-source ASM solution available
- CoalFire Attack Surface Management An ASM tool that has its assessments looked over by an actual human analyst.
- CyCognito Attack Surface Management Automation-packed tool that combines ASM and vulnerability management.
- ImmuniWeb Discovery An ASM tool with a lot of potential that comes with vendor risk tracking.
Doing this manually is nigh-impossible in small businesses, and is completely unfeasible for larger ones. Because of this, companies rely on attack surface monitoring tools to make it easier and more efficient. To ensure you’re protected against cyber threats, you need to have a solid grasp of what your attack surface is, as well as which parts of the said surface are at the greatest risk.
Why Use An Attack Surface Monitoring Tool?
Attack surface monitoring tools are necessary for medium to large businesses to attain a solid grasp of their attack surface. These tools provide ASM (attack surface management,) a crucial element of cybersecurity.
Attack surface management is a continuous process. Cybercriminals are always discovering new exploits, because of this, we have to stay vigilant when it comes to our protection. ASM consists of two distinct research phases:
- Assigning each piece of data you know a sensitivity ranking
- Gaining an accurate software inventory
Once this is complete, an attack surface monitoring tool will start looking for typical attack vectors that malicious agents use. DevOps environments should integrate attack surface monitoring into the CI/CD (Continuous Integration/Continuous Delivery) pipeline to ensure compatibility with brand-new functions, apps, and features.
Since attackers are always working on new avenues of attack, ASM has to continuously improve upon itself. Because of this, many tools are continuously updated from a database or via an AI to keep pace with attackers.
Although attack surface monitoring is a relatively new field, it can give you a massive cybersecurity advantage over your competitors. However, this also means that there hasn’t been enough time for tools to reach their peak. With that being said, a vulnerability scanner with software vulnerability coverage can work as a replacement for an ASM tool in a pinch.
Using an IDS (Intrusion Detection System) alongside an ASM is recommended, as IDSs will look at your entire network searching for incidents. Naturally, Data Loss Prevention software also synergizes very well with ASM tools. As always, it’s not enough to have one kind of tool protecting your entire network.
The Best Attack Surface Monitoring Tools
Sometimes, the line between vulnerability management and monitoring tools and attack surface monitoring tools can be quite blurry. Because of this, many vulnerability scanners are advertised as ASM software. In the same vein, many vulnerability scanners offer ASM without specifically stating they do.
In this article, there are a few criteria that we will be following to decide which tools to consider, as well as how to rank them. These are:
- Whether or not the tool looks for software vulnerabilities
- Whether or not the tool is capable of identifying outdated software versions
- Whether or not the tool can log data access by software and other metrics
- If the tool can tell which is which between regular and suspicious user activity
- How good the tool is at reducing the risk of data leaks
- Whether or not there’s a free trial
- How good the tool is at providing a comprehensive look at your entire data surface
- The quality of the tool’s UI, as well as user-friendliness
- How scalable the tool is
1. Intruder – FREE TRIAL
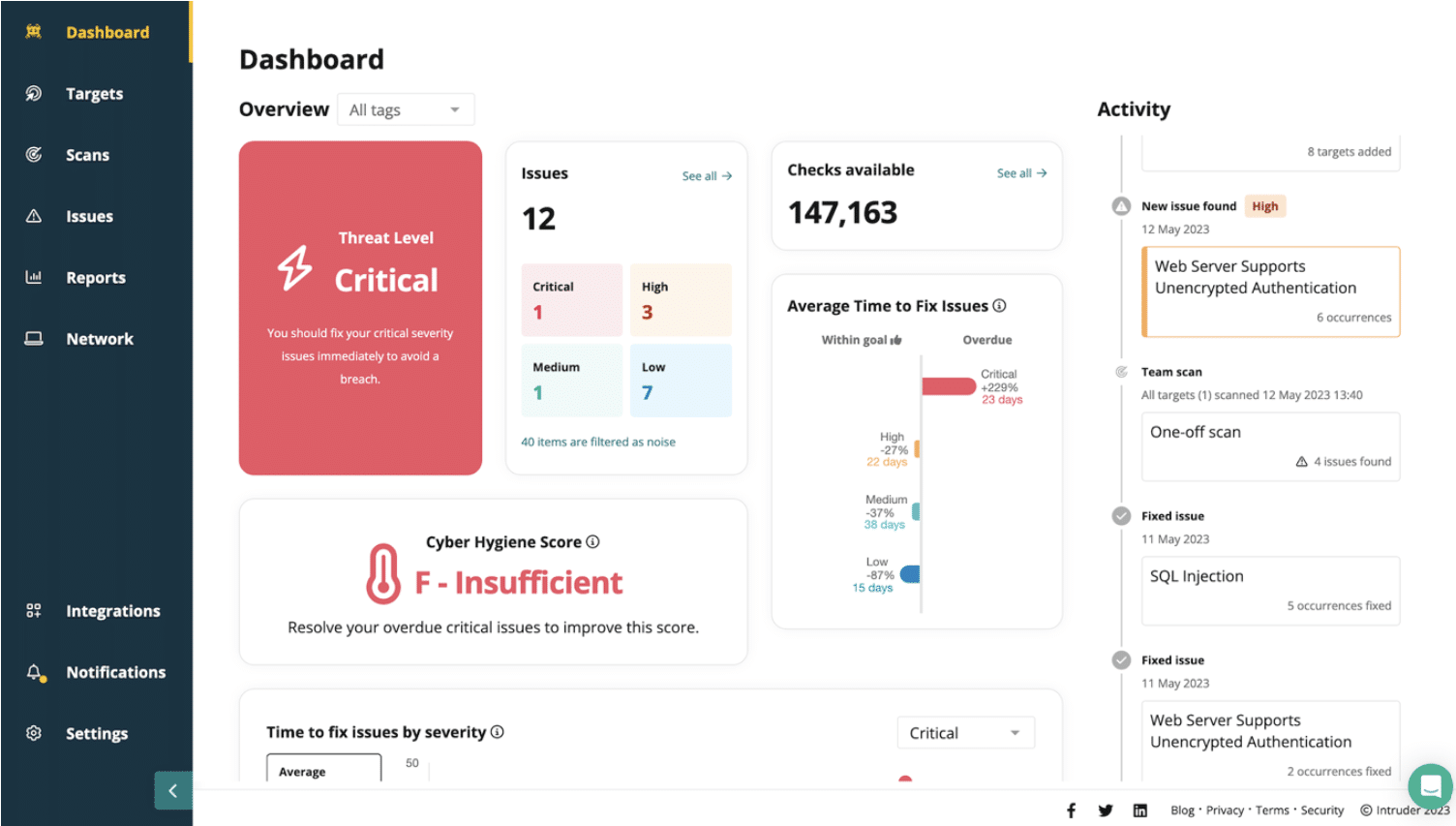
Intruder provides a security framework focused on simplifying vulnerability and attack surface management. It persistently monitors the attack surface, identifying potential vulnerabilities and entryways. By conducting more than 140,000 checks, it integrates smoothly with recognized scanning tools such as OpenVAS and Tenable, enabling users to pinpoint significant vulnerabilities, like an unguarded database.
Key Features
- Provides two vulnerability scanners with the cheaper of the two running once a month and the more expensive scanner for frequent, scheduled scans or on-demand operations.
- Has an option for internal scanning of endpoints and networks with the Tenable vulnerability manager
- Add-on option to get Web application and API security testing
The external scanner is able to probe your network from across the internet, looking for ways in. It will also check on your cloud services that are hosted on Azure, AWS, or GCP. The Intruder package can also be used for Web application and API security scanning through an add-on that is available to all editions. This can be set up as a continuous tester on a CI/CD pipeline.
Pros:
- Options for monthly, frequent, or continuous scanning
- The system dashboard is accessed through the Intruder website
- The platform generates a cyber hygiene score after each scan
- Reports can be used to prove to third parties that your business is secure
Cons:
- You need to upgrade to the higher plans to unlock more powerful features
The vulnerability scanner will look at the services that support your websites as well as check on the security of your network. For example, it will assess all SSL certificates and let you know if one is about to expire. The services of Intruder also extend to a human penetration testing team that you can hire for an in-depth system security check.
You can assess the attack surface monitoring system with a 14-day free trial.
EDITOR'S CHOICE
Intruder is our top pick for an attack surface monitoring tool because it caters to all types and sizes of businesses. Every business that has a connection to the internet needs at least a monthly attack surface scan to ensure that it is not vulnerable. Companies that have extensive Web assets, such as websites or Web applications need to ensure that they have thorough attack surface monitoring in place. In such cases, one of the two top editions of the Intruder system would be appropriate. Companies that develop and run Web applications should consider adding on the dynamic application security testing option.
Download: Access the 14-day FREE TRIAL
Official Site: https://portal.intruder.io/free_trial
OS: Cloud-based
2. ManageEngine Vulnerability Manager Plus – FREE TRIAL
A security application called ManageEngine Vulnerability Manager Plus aids companies in finding and patching weaknesses in their network and systems. It utilizes vulnerability scanning to find potential flaws, such as outdated patches or insecure setups, and it produces thorough reports on the findings.
Key Features
- Delivers thorough reports on the outcomes after scanning the network and devices for potential vulnerabilities, such as missing patches or vulnerable configurations.
- Gives a thorough list of every device connected to the network
- Advises on how to deal with found vulnerabilities, along with detailed instructions for remediation
To aid businesses in keeping their IT infrastructure secure, Vulnerability Manager Plus also has capabilities like asset management, patch management, and compliance reporting. It offers advice on how to address found vulnerabilities, along with detailed instructions and connections to relevant sources.
Pros:
- Great for continuous scanning and patching throughout the product lifecycle
- Robust reporting can help show improvements after remediation
- Flexible – can run on Windows, Linux, and Mac
- Backend threat intelligence is constantly updated with the latest threats and vulnerabilities
- Supports a free version, great for smaller environments
Cons:
- Vulnerability Manager Plus is very detailed, and best suited for enterprise environments
One way Vulnerability Manager Plus can be used is for regular vulnerability scanning to identify potential issues in an organization’s network and devices. If any vulnerabilities are detected, the software can provide a report and guidance on how to fix them. By proactively identifying and addressing vulnerabilities, organizations can improve the overall security of their network and devices.
ManageEngine Vulnerability Manager Plus comes with a 30-day free trial.
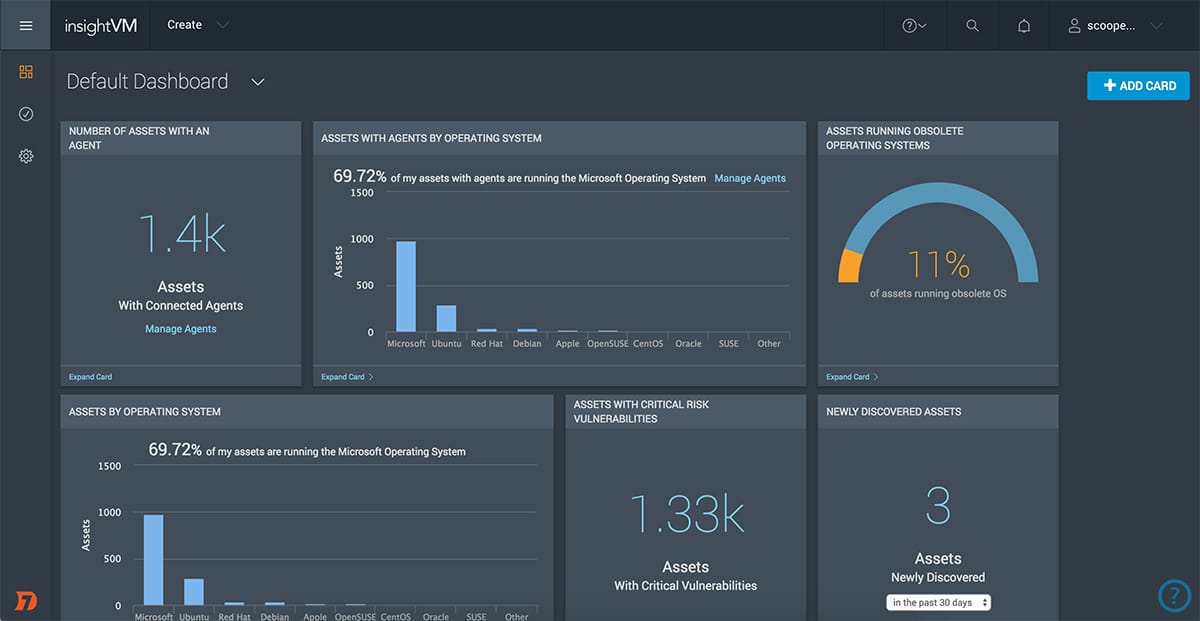
3. Rapid7 InsightVM
Although Rapid7 InsightVM is technically a vulnerability manager rather than an attack surface monitor, it has a variety of features that make it an excellent stand-in for a dedicated attack surface monitor.
Main Features:
- Third-party risk assessment system
- A vulnerability scanner with a variety of ASM features
- Slick, modern user interface
- Robust alerts system
- Can be easily integrated with a variety of other Rapid7 tools
- Made by a reputable company in the field
- Entirely cloud-based
- Easily scalable
Rapid7 InsightVM is capable of monitoring both on-premises devices as well as cloud and virtual systems. This means that it can reach every nook and cranny of your network with ease. Furthermore, not only is the Rapid7 a cloud-based tool, but it can check multiple networks at once. It can easily look over endpoints in remote areas or the homes of your remote employees.
The Rapid7 uses its innovative Project Sonar for most of its attack surface assessment, management, and monitoring features. Project sonar collects data loss event notifications and info on other cybersecurity problems from a variety of sources and creates a database of them. It can then form a 3rd-party risk assessment for businesses that run services used by their client. All in all, this provides as many ASM features as most dedicated tools, which is why we feel comfortable including Rapid7 InsightVM in this list.
The InsightVM is only one out of a variety of Rapid7 tools all of which can be easily integrated. The best one to supplant the InsightVM is their SIEM tool that provides a threat intelligence feed. This will help you spot vulnerabilities ahead of time and gain insight into common attack vectors being used on your competition.
All in all, the Rapid7 InsightVM is the best all-rounder choice, being good for small and medium businesses alike, and providing both ASM and vulnerability scanning features. With that being said, it’s a bit hard for beginners to learn how to use it.
The Rapid7 InsightVM comes with a free 30-day trial!
4. FireCompass Attack Surface Management Platform
FireCompass Attack Surface Management Platform is a new tool in the ASM area. Despite that, their dedicated ASM solution seems to be offering a lot of features that any business serious about attack surface monitoring needs.
Main Features:
- Creates inventories and discovers exposed parts of your infrastructure
- Reduces effective attack surface
- Real-time alerts system
- Extremely modern, both in UI and intuitiveness
- Quite beginner-friendly given its scope
- Focused on medium and large businesses
- Attack surface mapping features
The biggest reason for it placing below the Rapid7 InsightVM is that it simply hasn’t been out for long enough for us to be certain about recommending it against existing industry giants, however, the tool shows a lot of promise.
The FireCompass focuses on providing visibility into your attack surface for you to better understand your assets as well as the risks associated with each one of them. The tool focuses on catering to medium to large businesses. It provides excellent inventory creation features and is always on the lookout for exposed vulnerabilities, infrastructure, or domains/subdomains.
One of its most useful benefits is its dashboard, as it automatically prioritizes issues and sorts them into one of three categories: “High”, “Medium”, and “Low” importance.
All in all, an amazing ASM solution that can easily compete against its older competitors. With that being said, there’s only a limited number of free trials, lasting for an amount that is left unstated on their site.
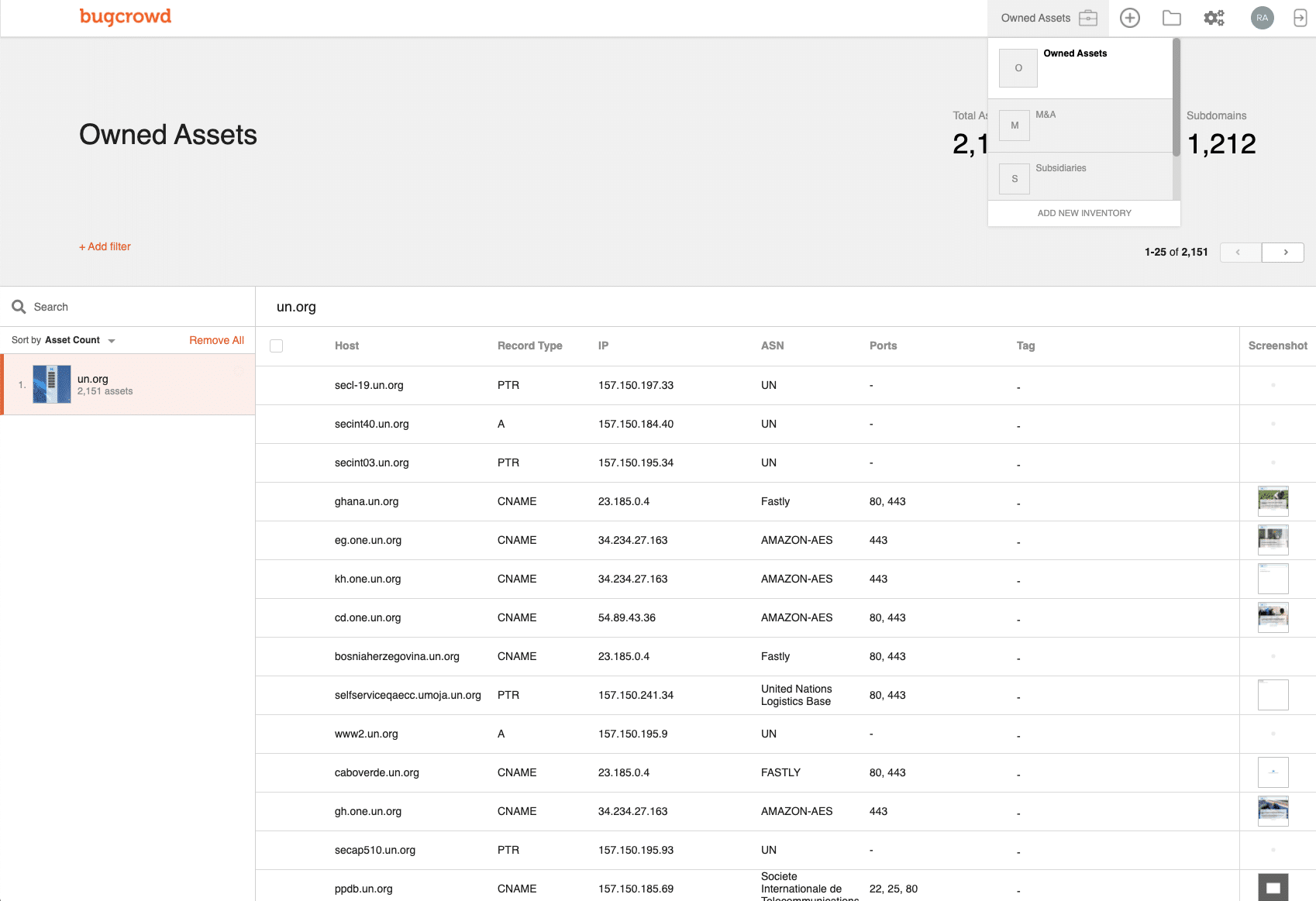
5. Bugcrowd Asset Inventory
Bugcrowd Asset Inventory is an extremely creative tool created by an organization of white hat hackers. This automated solution is a crawler that looks through linked software packages and can be used for pen testing to find the services and software a system uses. The Bugcrowd then goes through all of the APIs and microservices connected to the surface it’s going through and checks them for vulnerabilities.
Main Features:
- Will detect assets you’re unaware of on your system
- Simple but effective alerts
- Cloud-based
- You can commission human-based searches of your system
- Dedicated ASM tool
- Built by experts in the field
- 24/7 customer support
Bugcrowd has stated on its site that one-third of all successful cyberattacks come through a piece of software or service that the affected firm’s IT department isn’t even aware they’re using. Since it’s impossible to protect systems that you’re not aware of, Bugcrowd is always on the lookout for these unknown assets and will alert you if it finds a security risk associated with any of them.
In case you’re looking to get a personalized experience, you can commission a human-based search of your system. This is a pen-testing exercise where Bugcrowd puts a bounty on your companies’ system and invited some of the world’s best white hat hackers to break into it, giving a reward to the first one to manage this.
The Bugcrowd Asset Inventory isn’t very easy to use for untrained technicians. Furthermore, the only way to get a free trial is to request a demo from the company.
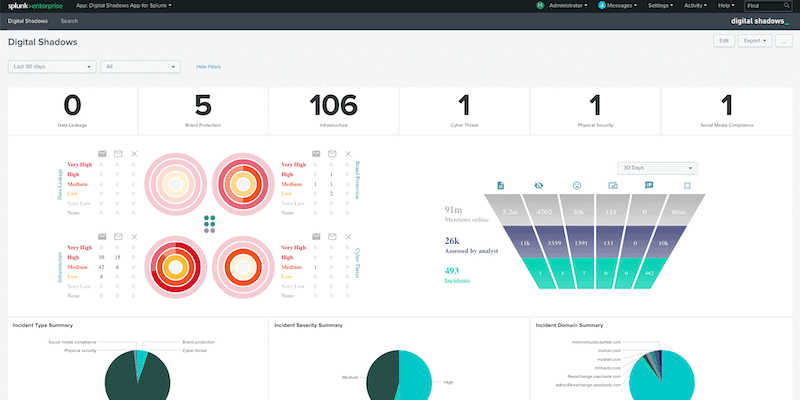
6. Digital Shadows SearchLight
The Digital Shadows SerchLight is an ASM tool that looks at a client’s total software assets and compares it to intelligence shared by known malicious users. This is an excellent tool to use to ensure you’re always staying vigilant against ever-improving threats. While most threat intelligence feeds simply record attack vectors that have worked against other firms, SearchLight also alerts companies when an attack is imminent.
Main Features:
- An extremely innovative approach to cybersecurity
- Alerts you when an attack is imminent, unlike most of its competition
- Excellent dashboard
- Fairly simple to use even for non-technical users
- Very accurate in its assessments
All you need to do to get SearchLight working is to register each of your outward-facing network components and include its details like its IP address, domain, etc. Then, it will constantly keep an eye out for any malicious agents mentioning that name. For example, SearchLight would be able to pick up an employee’s details or login credentials being spoken about on the Dark Web.
SearchLight analyzes all of the data it gets using its crawler and data analytics capabilities, finding potential attacks on clients that it’s protecting. The kind of data that it detects can indicate the attack vector a hypothetical malicious agent would use. Once it finds this, SearchLight alerts the client about which system defenses to harden in anticipation.
SearchLight is not a complete ASM solution. However, it’s a great addition to any ASM strategy. The tool comes with a one-week free trial.
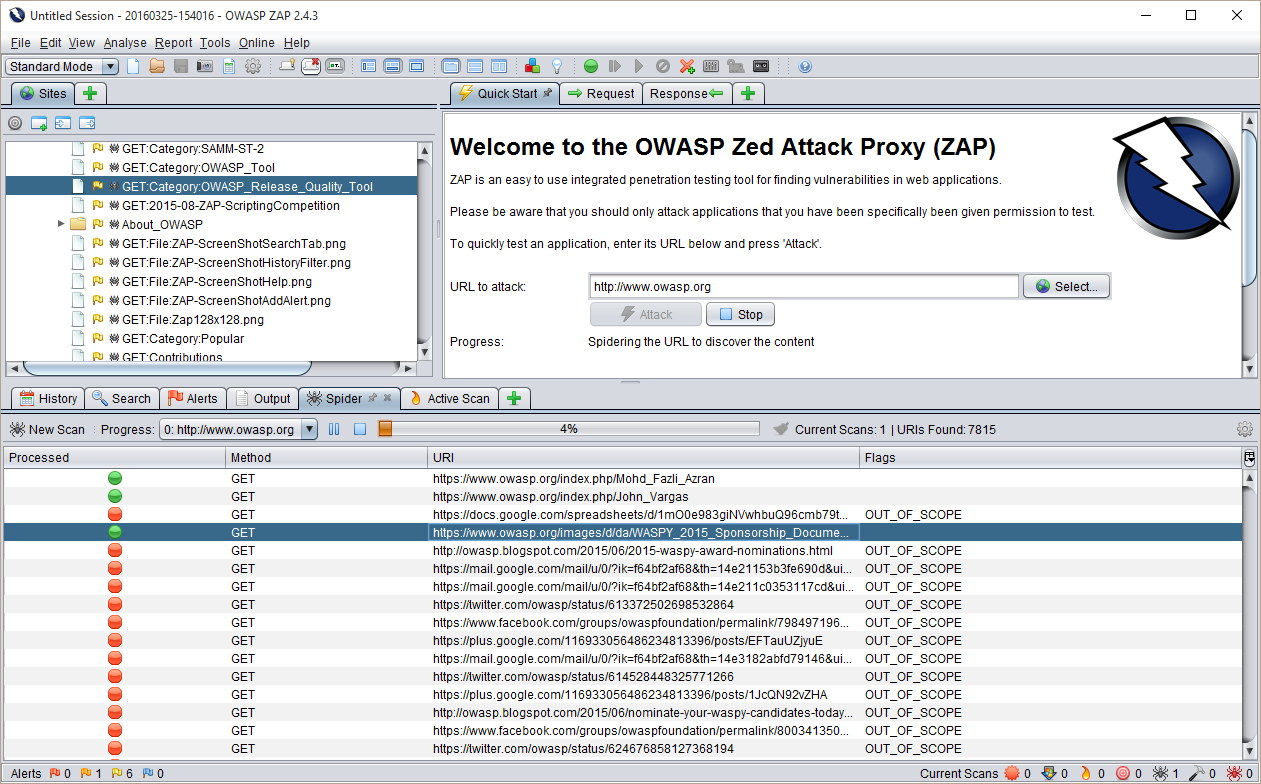
7. OWASP Zed Attack Proxy
OWASP Zed Attack Proxy is the first free tool on this list. Being open-source, the tool is extremely customizable. It provides a very efficient way to look through your website for the most common threats. Once a website is plugged in, it will immediately search it for the presence of any of OWASP’s Top 10 threats.
Main Features:
- Completely free and open-source
- Available on macOS, Windows, and Linux
- Can store application code, making finding controversial changes easier
- Helpful community
- Excellent for SMBs
While this might not seem very significant, a vast majority of cyberattacks come in the form of one of these threats, with the OWASPT Top 10 list being a major cornerstone for most vulnerability scanners.
The second OWASP project that can be easily plugged into the Zed Attack Proxy is the Attack Surface Detector. This is what turns this tool into a true ASM solution. The Attack Surface Detector is capable of tracing through APIs and Web services, which makes it an excellent discovery utility for attack surface analysis.
The detector will locate the host of each discovered application, as well as log its parameters for the call and all of their data types. It can also scan an application and store its code, making recovery much simpler. You can also routinely rescan the application, comparing its code to its stored version, which can make finding changes that can introduce new vulnerabilities a breeze.
The Zed Attack Proxy does lack some of the raw power and polish that its paid counterparts have.
8. CoalFire Attack Surface Management
CoalFire Attack Surface Management is one of the few tools out there that accurately assesses the risk that easy to integrate APIs and quick-to-install plugins provide. Pretty much all companies these days take advantage of these, however, few of them think about whether there are vulnerabilities within them.
Main Features:
- All results are looked at by a human analyst
- Considers all of the different circumstances and operating procedures in place within your business.
- Creates an inventory asset of everything that goes into your applications
- Pays attention to APIs and plugins
Once a website is online, it’s very difficult to rewrite it or make major changes. CoalFire makes finding what external services are integrated with the website a breeze. Its automated processes are capable of discovering all asset chains that contribute to your systems. Finally, it uses a human analyst to ensure that these findings are accurate.
Once it has assembled an asset inventory, you can think about a proper defense strategy, and whether or not all of the integrations are necessary to have.
With that being said, the tool doesn’t have a SIEM or intrusion detection system in place. However, it will guide how you should defend against hypothetical threats. All in all, this is a great supplementary tool for an ASM strategy.
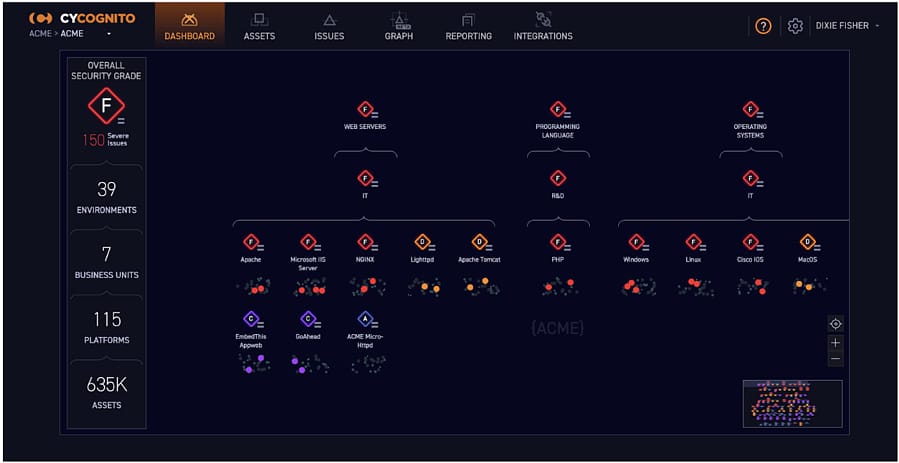
9. CyCognito Attack Surface Management
CyCognito is a cloud platform comprised of a variety of tools, including an attack surface manager and vulnerability manager. CyCognito works as an external attack surface monitor.
Main Features:
- Automation features supported by security analytics experts
- Third-party risk assessment
- Both a vulnerability manager and attack surface manager
- Ranks all of the potential risks on your system
- Modern user interface
The tool will find front-facing data, web services, and principality websites. From that initial assessment, the tool will look through the APIs and services contributing to them. This feature by itself is invaluable, as you’ll know exactly what code is contributing to your sites, as well as the companies behind them.
Another excellent feature is its third-party risk assessment and attack surface monitor. CyCognito automatically attempts hacks on all points within the chain of services contributing to your sites, looking for any weaknesses. This is excellent in case an API you’re using gets an update containing vulnerabilities. Then, the system establishes a ranking of the individual units’ risk and tells you which of these it thinks you should prioritize.
CyCognito doesn’t have a free trial, but you can request a demo from the company.
10. ImmuniWeb Discovery
ImmuniWeb Discovery is another combo of a vulnerability scanner and an attack surface monitoring tool. The ImmuniWeb finds all of your on-premises and cloud software assets and then traces through APIs to find the code’s host.
Main Features:
- Scans the Dark Web for mentions of your firm or peripheral software
- Multiple pricing plans(Express Pro, Corporate, Corporate Pro)
- On-demand scans of third-party systems in the full version
- Vendor risk management tracking
All in all, the ImmuniWeb Discovery has a lot of potential, but it can be a bit clunky to use and set up, in addition to lacking a free trial. Instead of this, you’ll have to request a demo if you want to try the tool out.
It has a vendor risk management feature, tracking any incidents that any of the vendors you rely on have had in the past. It also looks through the Dark Web searching the most well-known hacker communication channels for any mentions of software or entities connected to your business.
This makes it an excellent tool that covers both your internal and external weaknesses. It will also generate recommendations and alerts based on what it detects.
Closing Words
Attack surface monitoring is growing increasingly more important as businesses continue to rely on APIs and third-party plugins. Today we’ve tried to isolate the best tools to make this process more efficient. Since attack surface monitoring is a relatively new field, we’ve included some non-dedicated tools that fulfill most requirements to be an ASM tool.
As always, the right ASM tool for you will depend on your needs. Depending on the needs of your business, our number nine pick might be your number one. However, we’ve tried to ensure that the first few picks are ones that you can’t go wrong with.
What is your favorite attack surface monitoring tool?
What feature do you wish was more commonplace among them?
Let us know in the comments below!