SIEM, or Security Information and Event Management tools, are there to give you an accurate assessment of your network security.
Now, there are various SIEM tools out there, and picking the right one can have a meaningful impact on your network security. Because of this, we’ve assembled this guide to give you the cream of the corp in the world of SIEM tools.
Our list for the best SIEM tools is as follows:
- SolarWinds Security Event Manager – FREE TRIAL Made by the reputable SolarWinds company, the SEM is an excellent SIEM tool for beginners.
- Heimdal Threat Hunting and Action Center – ACCESS DEMO This SIEM service is integrated into a threat intelligence platform that also provides automated responses.
- ManageEngine Log360 – FREE TRIAL – This package is a SIEM plus other system security tools with compliance auditing and reporting included as well. Runs on Windows Server.
- Datadog Security Monitoring – Giving an excellent all-rounder approach to SIEM, Datadog is a perfect SIEM tool regardless of whether you’re simply starting strong or if you’ve got SIEM veterans in your firm. It gives you access to everything you’ll need to know and more, all packaged up in an intuitive dashboard with at-will visualization. To top it all off, so you don’t even need an on-site installation.
- Splunk Enterprise Security – One of the most popular SIEM tools worldwide supporting both Windows and Linux.
- ManageEngine EventLog Analyzer – A SIEM tool specializing in analyzing and organizing logs.
Important SIEM Features
Although SIEM systems aren’t without fault, they’re one of the biggest tells that a firm takes cybersecurity seriously and that they’ve chosen to implement a good policy. 90% of the time, you’ll find that attacks on your network don’t have any surface-level hints. Because of this, it’s often better to use log file data to spot these. This naturally leads to SIEM tools becoming one of the pillars of network security.
You’ll find that a lot of security-oriented applications work on small-scale issues. While they’ll often solve more minor threats, they’ll also miss the bigger picture. A simple IDS (Intrusion Detection System) by itself can only really keep track of packets coming in and out, as well as IP addresses. Similarly, you’ll find that service logs will only display user sessions and changes to any configs. SIEM takes these simple systems and puts them together to give you a much better look at any security issue by providing real-time monitoring and analyzing all event logs.
What Is SIM?
SIM, or Security Information management, also known as log management, refers to the collecting, monitoring, and analyzing data provided by the computer logs.
What Is SEM?
SEM or Security Event Management refers to managing network events. This includes a variety of security processes, such as threat visualization and real-time analysis.
What Makes SIEM Important?
SIEM has started to take a more prominent place in most modern businesses’ cybersecurity throughout the last few years. The biggest reason for this is that all trackers and users leave behind a virtual trail in the log data. SIEM tools take advantage of this data to analyze attacks and other network events. Having a SIEM system will let you know when an attack occurred and how you were attacked and what caused it to be possible.
Most enterprises constantly update and upscaling their IT infrastructure, making SIEM more and more critical. Although it’s a common belief that firewalls and antiviruses are often enough to give total protection to a network, zero-day attacks are still quite common when you rely on these measures alone.
SIEM tools solve this problem by precisely detecting suspicious activity compared to past network behavior. This gives SIEM the capability of distinguishing between regular network use and an attack.
Using SIEM will also aid you in complying with various cyber management regulations, becoming increasingly common across many industries. SIEM tools give you the best way to satisfy regulatory requirements and provide you with log transparency you can use to gain a better insight into your security and improve it.
What Does A SIEM Tool Need?
SIEM tools are quite different from each other. Because of this, no SIEM tool is ideal for all businesses. A SIEM tool that is a perfect fit for one enterprise might be found lacking at another. However, there are some key features that SIEM tools will need to qualify for this list.
The Ability To Manage Log Data
With log data management becoming increasingly important for enterprises, no SIEM tool is complete without it. You’ll need your tool to collect log data from many different data sources using additional recording and categorization methods. When you’re deciding on which SIEM tool to use, you should go for the one that can normalize your data well. With that being said, if you find one that you love in all aspects but this one, you can rely on some third-party tools to help you manage log data.
When your data is normalized, the tool will then quantify it and contrast it to the previously recorded information. The tool will then take advantage of this to find patterns within malicious behaviors and alert you to react to them. Your analysts can also make different criteria in most tools for you to be even more prepared for future threats.
Quality Compliance Reporting Capabilities
If you’ve got a SIEM tool that has excellent compliance reporting capabilities, that’ll be a massive convenience for your enterprise. Most good SIEM tools will have a report generating functionality to aid you with conforming to different regulations.
The source of the requirements you want to comply with will be a significant factor in selecting the ideal SIEM tool for you. There are many standards these days, ranging from HIPAA to PCI, NERC, DSS, and many others. If your SIEM tools can help you meet them, that will save you valuable time.
Threat Intelligence Quality
If malicious behavior occurs on your network, you’ll want your SIEM tool to give you a detailed report on how it happened. This data can aid you in refining the internal workings of your network to eliminate the chances of that attack repeating. If a SIEM tool doesn’t help your enterprise prevent future threats, you should look for a different one.
Customizable Alert Conditions
What looks like regular network activity on one network might look like malicious activity on another. Setting criteria for your SIEM tool’s alerts is crucial for getting the most out of its threat intelligence. The more you can customize your SIEM tool’s alert conditions, the more it’ll be able to help you deal with brand new threats. Cyber-attacks are evolving daily, so you should be using a SIEM tool that’s capable of matching their pace.
Furthermore, you’ll want a tool that will let you restrict the number of alerts you get simultaneously. If you’re overflowing with different alerts, your cybersecurity team will be a lot less efficient in dealing with issues. If you’re unable to change alert conditions, you’re setting yourself up to dealing with waves of barely relevant alerts.
Intuitive Dashboard
Now, a SIEM might have excellent functionalities, but if they’re gated behind an unintuitive and difficult to use dashboard, that’ll lead to you wasting valuable time navigating through it. Furthermore, a good dashboard helps you have a much easier time finding threats.
A well-visualized dashboard lets a good analyst detect malicious behavior from a mile away.
What Are The Best SIEM Tools For You?
Before you pick your SIEM tool, you should do a breakdown of what you’re looking to accomplish using it. If you’re looking to get a SIEM tool mainly to help you meet regulations, then you’ll be evaluating report generation much higher than you will the tool’s alert system.
On the other hand, if your primary plan with getting a SIEM tool is to help you protect your enterprise from malicious behavior, you’ll need a tool with excellent normalization and customizable threat detection.
Since there are so many criteria you could be looking at when picking a SIEM tool, we chose to stick to some of the most important ones in this list. We evaluated the SIEM tools below based on the following:
- How good they are at gathering log messages as well as live data from traffic
- The quality of its log file management capabilities
- The data analysis utilities that the tool comes with
- Whether or not the tool provides quality report generation
- How easy the tool is to use and install
- Whether or not there’s a trial period for you to get used to the tool
- How much value it provides with its price
The Best SIEM Tools
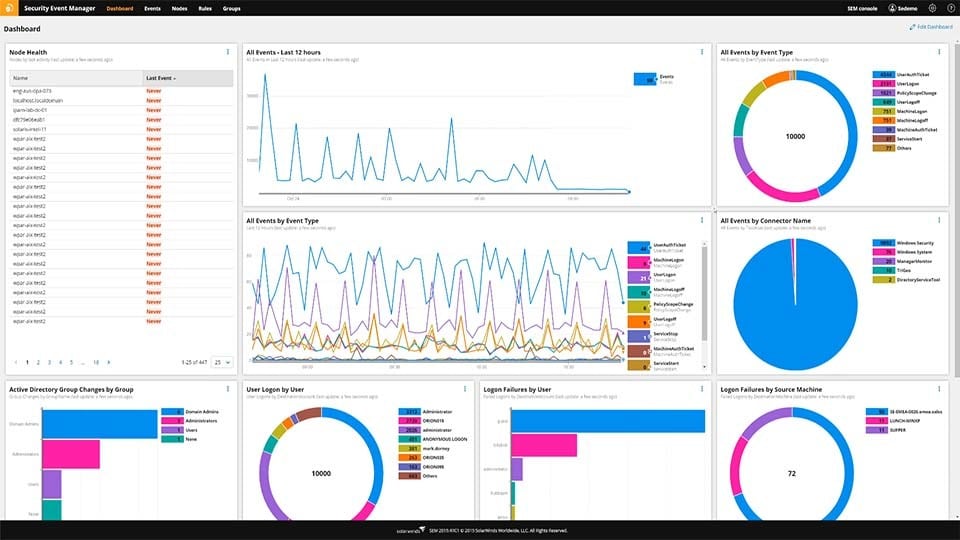
1. SolarWinds Security Event Manager – FREE TRIAL
If you’re looking for an entry-level SIEM system, then the SEM or SolarWinds Security Event Manager might just be what you need. The tool will give you all of the central features that a more advanced SIEM tool might have in a newbie-friendly chassis. The SEM features excellent log management and reporting features, which are the two most important things to have for a beginner-oriented SIEM tool.
If you’re looking to protect a Windows system, then SolarWinds will give you a detailed breakdown of all incident responses. It makes excellent use of Windows’ event logs to help you get a better grip on protecting your network against a variety of different threats.
Main Features:
- The SEM automatically searches your log files for malicious activity
- It provides anomaly detection in real-time
- The tool supports historical analysis
- It has a long, 30-day extended free trial
- Its log filtering is kept simple without requiring you to learn a specialized query language.
- It provides various templates that let you use the tool without spending much time setting it up
One of SEM’s most significant selling points is how well-crafted its dashboard is. With all of the simple visualization tools, finding anomalies is made as easy as it can be. Furthermore, SolarWinds offers 24/7 support, meaning you can contact them at any time if you need help.
With that being said, SEM is mainly geared towards enterprises, so smaller businesses may feel like it isn’t fulfilling its purpose as well as it could be.
The SEM deserved its spot on this list with its excellent use of data visualization and its smoothness running on Windows Server. Its real-time alert and response functionalities make it easy for you to get a grip on your infrastructure. SolarWinds Security Event Manager is offered on a fully functional 30-day free trial so you can check if it is the right tool for you before purchase.
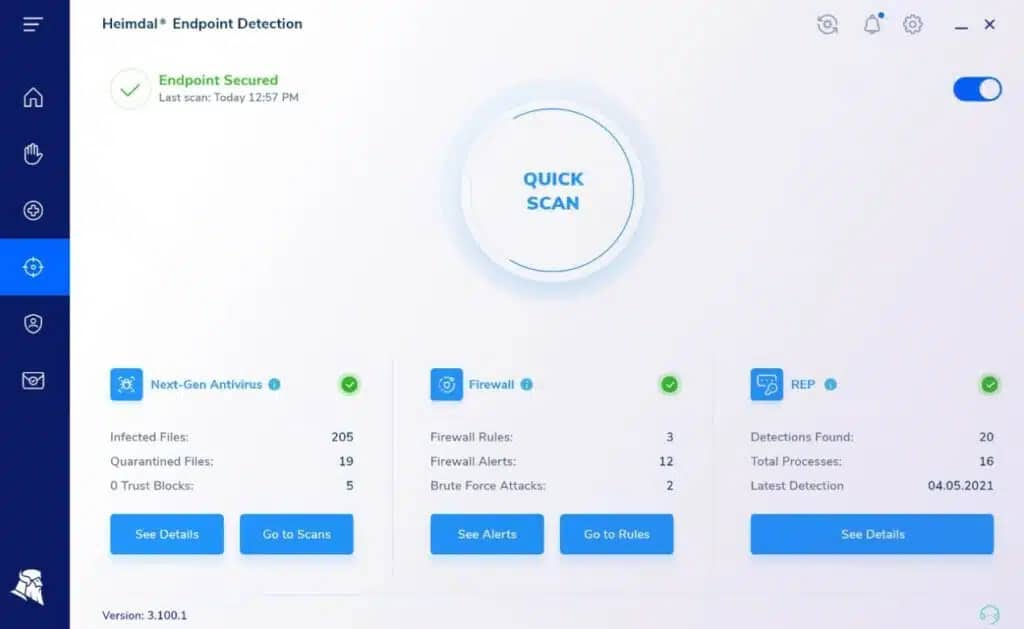
2. Heimdal Threat Hunting and Action Center – ACCESS FREE DEMO
Heimdal Threat Hunting and Action Center is based in the cloud and relies on the installation of Heimdal on-premises products. The tool receives activity reports from those on-site tools, consolidates them, and then searches through them for threats. The platform also provides a library of playbooks that will trigger automated responses on the discovery of a threat.
The cloud package coordinates the activities of the Heimdal Next-Generation Anti-Virus, which is an on-premises system that runs on Windows, macOS, and Linux. The NGAV includes a mobile device management (MDM) tool that manages devices running Android and iOS.
Main Features:
- Scans for threats on workstations and mobile devices
- Includes endpoint vulnerability scanning
- Forms a hybrid cybersecurity package
- Consolidates uploaded activity reports
- Implements automated responses
- Provides a private threat intelligence service
- Offers user activity tracking
- Cloud-based dashboard shows system activities
Apart from instances of the NGAV, the client must have at least two other Heimdal tools operating on a site. The options for these other two tools are Network Security, Email Security, Patching & Asset Management, or Endpoint Security.
While gathering activity data for the SIEM, the cloud dashboard also summarizes that information and shows it in the cloud dashboard. So the Action Center provides a system-wide activity overview as well as threat detection.
The SIEM module is called the XTP Engine, where XTP stands for Extended Threat Protection. This is linked to the Action Center’s rule base that selects a suitable playbook if a threat is detected. The service implements responses directly with the device that is found to be under threat and also informs all other devices on the network to be aware of a potential problem. Actions to shut down a threat might involve work from several devices.
The Heimdal Threat Hunting and Action Center form part of a suite of cybersecurity tools. Heimdal doesn’t publish a price list and there is no free trial. However, you can access a demo to find out more about the Threat Hunting and Action Center.
3. ManageEngine Log360 – FREE TRIAL
ManageEngine Log360 is an on-premises SIEM system that includes six other ManageEngine tools. Those complimentary systems collect and consolidate logs, protect files from tampering, audit Active Directory, and track file movements.
Log360 collects log messages in all formats from more than 700 applications and operating systems and then converts each arriving message into its own neutral format. As this consolidation process completes, log messages feed into the SIEM analysis engine. This looks across devices and applications for correlations of indicators that suggest a threat. The SIEM focuses on intrusion detection while other tools in the Log360 examine activity for insider threats and unauthorized file manipulation.
Main Features:
- Monitors network endpoints and cloud platforms, such as AWS and Azure
- Real-time analysis of logs plus a data viewer that supports manual analysis
- Active Directory change tracking
- File integrity monitoring
- Active Directory auditing and assessment
- USB device control
- Data loss prevention
- Compliance auditing and reporting
The Log360 service is built for busy IT departments and it has capabilities to integrate with some of the major service desk packages. Three include ManageEngine ServiceDesk Plus, Jira, and Kayoko.
When the system detects suspicious activity, it generates an alert. This is displayed in the dashboard of the service but you can also get that alert forwarded as a notification by email, SMS, or through your ticketing system. This means that you don’t have to place a technician watching the Log360 dashboard to spot problems. The system will track events so you can assume everything is OK unless your staff gets a notification.
Logs are stored in a meaningful directory structure with log files rotated periodically. This makes historic data available for auditing, which is a requirement of many data protection standards. The Log360 package also includes a compliance reporting module for HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA. The entire system can be adjusted to enforce the requirements of a specific standard through the use of a security policy template in the system configuration screens.
There is a Free version of Log360, which has all of the functions of the paid package but with volume restrictions. The paid plan is called the Premium edition and you can assess it with a 30-day free trial. If you choose not to buy at the end of the trial period, your installation switches over to the Free edition.
4. Datadog Security Monitoring
If you’re looking for an excellent all-rounder SIEM tool, then Datadog Security Monitoring might just be the tool for you. Supporting the integration of over 500 different vendors, in addition to its excellent pre-configured detection rules, makes it an ideal fit for new and experienced users alike. Datadog Security Monitoring handles security features in a specialized module. As a complete SIEM solution, the tool will monitor events as they happen while collecting them as entries to log files.
Furthermore, your local info will be gathered through an agent and uploaded to the Datadog server. This lets the tool analyze any notifications and organize them.
Main Features:
- The tool provides security event detection in real-time
- You can check different logs, metrics, or various other things from a singular, intuitive dashboard
- Its preconfigured settings are excellent for starting with a SIEM tool
- You can see all of the event records within its console
- The tool will keep and index any logged messages for 15 months
- You can extract or access any of the messages or files Datadog organized through its console
- You can start threat detection immediately
Being a cloud-based service, Datadog helps you ease up on the processing demands that an on-site SIEM tool would bring. Furthermore, it makes monitoring remote networks a breeze, packing an analysis module with an excellent set of predefined rules to find common attack patterns.
The Datadog also updates its detection rules without needing you to lift a finger. As they find new attack vectors, the tool is updated to combat them. This lets you worry much less about keeping your SIEM tool up to date with attack strategies, as they do this automatically. But if you feel the need to customize your detection or mitigation rules, Datadog lets you do this with ease.
With that being said, the Datadog isn’t entirely flawless. Being so cram-packed with different functionalities means that the wealth of features can feel overwhelming when you first start using it. However, its pre-configured rules will help you get through that hurdle.
Datadog gives you various specialized modules that you can deploy when you need them, or you can simply deploy them together in a suite. All of these modules are also able to share data on your system with each other.
These factors are put together to make it our top choice for an all-rounder SIEM tool with which you can’t go wrong.
Datadog offers a 14-day extended free trial.
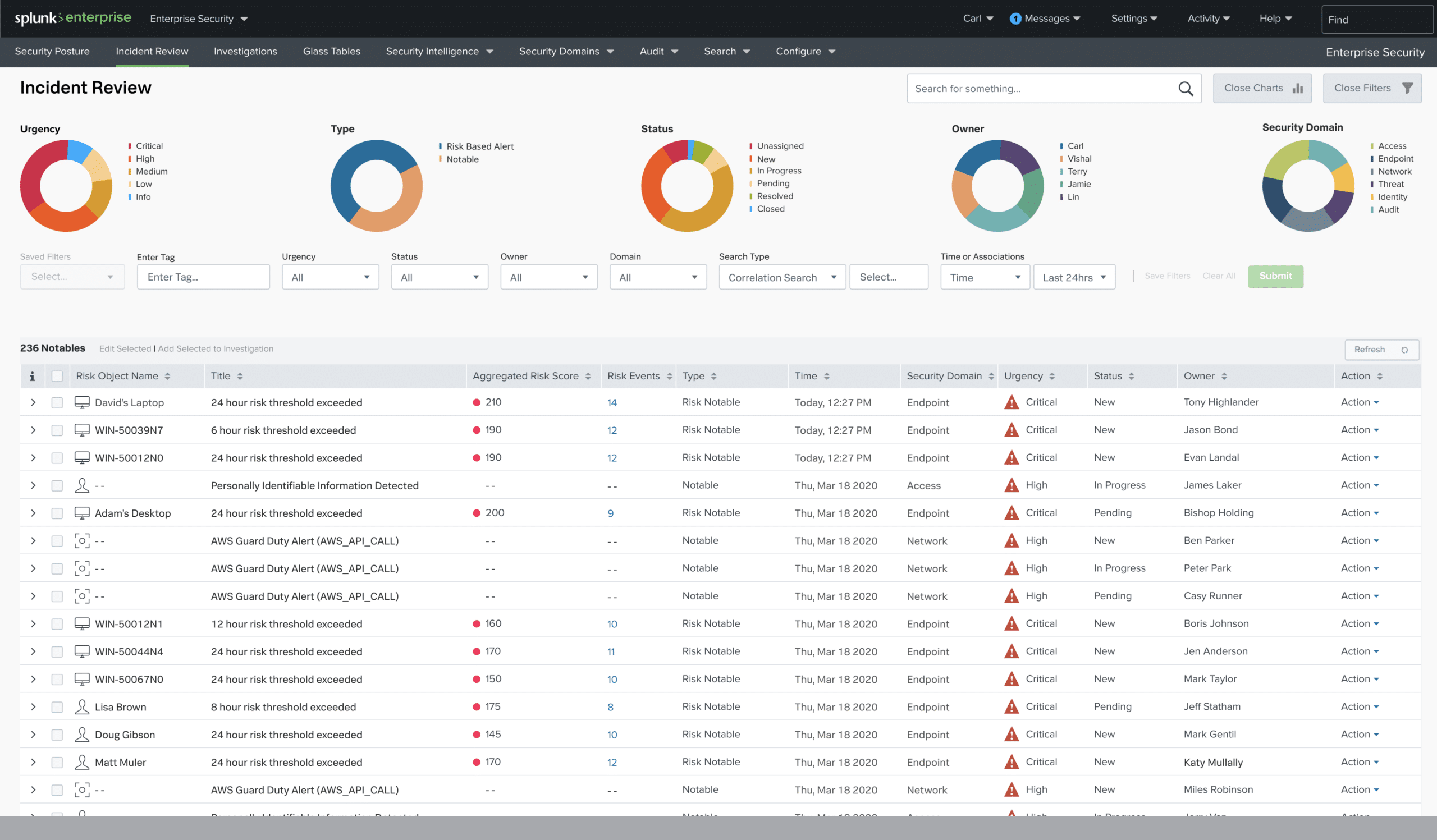
5. Splunk Enterprise Security
Available to both Windows and Linux, Splunk Enterprise Security is among the most used SIEM tools worldwide. Its defining characteristic is the quality of how well it incorporated analytics into the core of its approach. It will monitor all network and machine data in real-time and alert you when an attack occurs, and point out potential vulnerabilities ahead of time. It also allows you detailed customization of its alert system.
Main Features:
- You can monitor your network in real-time
- Splunk features an asset investigator utility
- Much like SEM, it has historical analysis capabilities
- The tool takes advantage of behavioral analysis to find threats undiscoverable through logs
- It sports a sublime UI, with a lot of visualization and customization
Now, Splunk does come with a couple of issues as well. The biggest in our eyes is their lack of transparency when it comes to its cost. To find out how much Splunk will cost you, you’ll need to ask the vendor for a quote. It’s also primarily geared towards larger enterprises than it is smaller firms.
Furthermore, the tool uses SPL for all of its queries, meaning you’ll need to learn that in addition to the tool’s essential functions.
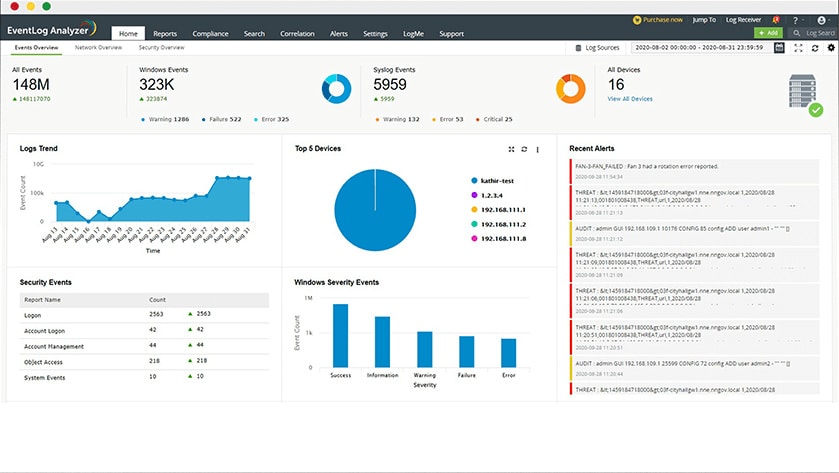
6. ManageEngine EventLog Analyzer
Another tool available both on Windows and Linux is the ManageEngine EventLog Analyzer. This tool made its niche in managing logs and ascertaining security and performance info based on them.
When the tool gathers Windows Event and Syslog logs, it’ll proceed to organize them and place them in aptly-named directories so that you can access them quickly and easily. It will then use other functionalities to keep these files away from being messed with.
Main Features:
- Collects Windows Event logs as well as Syslog messages
- It’ll detect malicious activity in real-time as it happens
- It has excellent log analysis functionalities
- Both Linux and Windows are available
- ManageEngine supports a variety of different standards like HIPAA, FISMA, PCI, and others
- Its intelligent alerting system makes it, so you get no false positives and helps you prioritize the most important events
- It has a free testing version
Despite all of these benefits, the ManageEngine does struggle quite a lot with helping new users get into the groove of it. If it’s your first SIEM tool, it’ll probably take a while to adapt to it. However, it does have a free version to test out and two others, the Premium and Distributed editions, with the second being network-based. You can get either of these versions with a 30-day free trial.
Closing Words
When choosing a SIEM tool, finding one that suits your tastes can be a real challenge. The four entries above all target a different audience, and chances are one of them should work for what your SIEM strategy is trying to accomplish.
Is there anything else you’d like to know about SIEM? Did we miss your favorite SIEM tool? Let us know in the comments below!