APIs are significant to today’s development world. Whether you’re working on mobile, web apps, or even internal apps for use in your company, you’re unlikely to avoid APIs as a whole. The very nature of an API makes it so that it exposes a lot of sensitive data like the PII (Personally Identifiable Information.) Due to this, API-based apps are slowly becoming one of the most targeted apps for attacks.
Today, we’ll be taking you through some of the most commonly asked questions about API security, as well as some steps you should be taking for your business to stay secure.
What Is An API?
An API, or Application Programming Interface, allows developers to “call” upon data from outside sources to work with the app they’re building. For example, a travel app might use an API to get information about prices in various airlines, car rentals, hotels, etc.
APIs help developers and companies by making the app development process more efficient. The sheer extent of the data that an app can easily access through an API is enough to make them worthwhile for most big-name companies out there.
APIs help providers as well, as they can generate income by making their data more valuable and charging for it.
In the end, the most significant benefit is reaped by the consumer. Consumers today are used to some simpler conveniences brought by APIs. But, on the other hand, the area is ripe for innovation, so many businesses are hopping onto the opportunity to turn a profit.
What Makes API-Based Apps Different?
- The server’s mainly used to have a data proxy
- Most rendering is done client-side rather than server-side
- APIs let attackers look “under the hood” of apps easier
- The state of the user is generally monitored client-side rather than server-side.
These and many other differences of API-based apps make their security quite a bit different. There are attack vectors out there targeting APIs specifically. API-based apps can also be weak to traditional vulnerabilities, so we need to take extraordinary measures to secure them.
What Makes API Security Important?
API security is crucial to any business taking advantage of them because APIs are connected to services and transfer data. This means that a hacked API quickly turns into a data breach.
Furthermore, in the last four years, we’ve seen the rate of API abuse problems double. A 2019 study by Micro Focus Fortify shows that 35% of the web apps they got to analyze had API abuse problems. It’s even more frightening when we look at mobile apps, where the rate of API issues was 52%.
Businesses are swiftly minimizing their use of more traditional, monolithic web apps. Instead, they either opt for modern implementations using client-side JavaScript and invoking server-side APIs or microservice-based architectures. Unfortunately, a direct consequence of this is units of functionality getting smaller, giving malicious agents more entry points to try and hack into your systems.
Why Using An API Is Risky?
Although using an API brings many benefits to your company, they come with inherent risks, especially for providers. The very design of an API means that outsiders can have access to your data. All APIs are connected to a server and its databases, giving them access to the data that your API-based app is using.
When it comes to the vulnerabilities that this presents, we can think of an API endpoint as akin to a web server. The more accessible and open the public’s access to the resource, the higher the chance that an attacker might pounce on the opportunity. The most significant difference is that websites still generally have some protection from malicious agents, such as user authorization.
One of the most significant problems APIs cause is that they give you little control options. Because of this, Gartner has estimated that API abuses will become the most frequent path attackers take to cause a data breach.
The worst-case scenario in these cases is that it doesn’t have to be just your data that is at risk. It can be your whole infrastructure. By taking advantage of an API vulnerability, some attackers will gain access to your network.
From there, if they can escalate privileges, they can escalate their attack in various unpredictable directions. A well-organized multi-level attack incorporating this can read to your business’s most precious data being lost or stolen.
With that being said, regardless of what route attackers take, they’re causing the same issue- a data breach. This can compromise your brand name and reputation and wind up with you facing some financial problems.
Most Common API-Targeting Attacks
In addition to the attack mentioned above vector, APIs are vulnerable to many of the same issues that network security experts have been battling for years. Although none of the below attacks are new per se, it’s still essential to ensure that your API is protected against them.
- Injection: An injection attack essentially entails the attacker inserting malicious code or a set of maliciously-inclined commands into your program. This is usually done in places where user input is expected, like login fields. An SQL injection is a specific kind of injection attack with the attacker trying to get into an SQL database.
The fix? Start validating and sanitizing all of the data in your API requests. You should also limit response data to prevent leaking.
- Cross-Site Scripting: XSS is a variation of an injection attack. It describes the insertion of a malicious script (usually made in JavaScript) into the code of your web application or webpage.
The fix? Validate your user inputs, and make sure you take advantage of character filtering and escaping.
- Man-in-the-Middle: A MitM attack is where the attacker intercepts data packets while traveling between two systems and impersonates them. This makes the attacker acting as a hardly-detectable proxy between the two systems. There are two places where a MitM attack can occur in an API context: Between the app and API and between the API and endpoint.
The fix? Start encrypting all of your traffic; this way, even if a MitM attack occurs, they won’t get anything from it.
- Distributed Denial-of-Service: A DDoS attack usually involves flooding a system with requests and traffic in a larger capacity than it can handle, rendering it unresponsive or entirely unavailable to users. In an API context, these are usually aimed at API endpoints.
The fix? Take advantage of rate-limiting, and start limiting the size of payloads.
- Credential Scuffing: This kind of attack refers to using stolen credentials to fool your API’s authentication functionalities.
The fix? Use rate limits to put brute force attacks in control, pairing them with an intelligence feed that can detect credential stuffing.
With that out of the way, what are some steps you could be taking to take your API security to the next level?
1. Keep Yourself Up To Date
To maintain API security, you need to know the newest tricks, and attackers use attack vectors. There are various places where you can get this information; for example, you can follow malware-related blogs, RSS feeds, and cybersecurity portals.
This is an excellent prevention measure as if your developers can configure the APIs to avoid widespread attacks. Then you’ll prevent them before they even try to target you; getting information from trusted avenues like OWASPs vulnerability lists (or our own) is a great way to stay informed.
2. Invest Into Authentication And Authorization
There are many APIs out there that have little or even no authentication or authorization to them. As a result, these APIs are ripe for exploitation. Many APIs appear as database entrances to attackers; because of this, you must know who is accessing what. In addition to this, you need to have the ability to reject them if you detect them as a malicious agent.
An excellent tool to take advantage of for authentication is OAuth. This is a framework that helps you make sure only authorized users are accessing your information. It also helps share information with a 3rd party without giving your credentials away.
OAuth is a tool that stops you from having to remember dozens of passwords. Instead, it gives every user a token given to them by a 3rd party server. This protects the customer as they don’t have to give away their credentials, and you don’t need to think about protecting your authorization data, as it’ll only take tokens.
Ensuring excellent authentication and authorization also makes you resistant to some more low-tech attacks. For example, an employee leaking a password is no longer as big a deal if you’ve got proper authentication facilities.
3. Use Encryption
In the 21st century, data encryption is a no-brainer. Simply encrypting your data can often be enough to dissuade attackers. After all, what’s the data going to do for them if they cannot read it?
Furthermore, encryption annuls the impact of some common cyberattacks like MitM attacks. With that being said, you’ll need to encrypt all of your data with a suitable encryption technique like Transport Layer Security. Furthermore, you’ll need to ensure only properly authorized users can decrypt the data.
4. Find Vulnerabilities In Your API
There’s no such thing as a piece of software without any vulnerabilities. Therefore, you must know your weaknesses on your own software.
To bolster your defenses against threats, you’ll need to know what attackers are most likely to target. Now, this can be hard to get to grips with, as you might be using hundreds of APIs at once. The simplest way is just to test your API rigorously before rolling it out. This way, you prevent day-zero attacks and make it easier for your team to fix the vulnerabilities found.
Another great way to do this is by having an in-house hack-a-thon where your employees look for the vulnerabilities themselves. Making this into a competition and having a prize (whether money, vacation days or the best cubicle) is a great idea as well.
5. Remove Any Unnecessary Sensitive Data
The best way to ensure that attackers don’t get a specific piece of information from your API is by making sure that it isn’t involved with your API in the first place. Unfortunately, it’s pretty standard for developers to simply forget to take out data like passwords or keys before an API goes public.
This element of human error can be corrected with reminders before an app is rolled out or by having developers check each other’s code. If you don’t do this, the worst-case scenario is that attackers can get to the core of your API and change it with you and your users being none the wiser.
6. Implement Rate Limits
The more popular an API gets, the higher the chances it’s going to face an attack. DDoS attacks, in specific, are almost a rite of passage among APIs.
DDoS attacks are made by repeatedly flooding your API with traffic until your server crashes. Implementing rate limits is the easiest way to mitigate the impact a potential DDoS attack will have on your API. These are limits to the number of times that your API can be called.
This way, the risk of your server crashing due to too many calls dramatically diminishes.
7. Pay Attention To Parameter Validation
Validating parameters makes sure that the data coming into your API is not harmful to it. To do this, you’ll need to create a strict set of rules that outline what inputs to the API are acceptable and then make all parameters going into your API validated by this ruleset. This way, you can lower the chances of your API being called maliciously.
8. Use An API Gateway
An API gateway is a management tool sitting between the client and the API. They are the easiest way to control and manage the traffic that comes into your API. Generally, having a solid API gateway can put in a lot of work, decreasing the attack risk. They will help you properly authenticate traffic and analyze if your API is being used maliciously.
9. Always Have A Threat Model
A threat model is essentially a simplified version of your most likely attacker. Having one is extremely useful for identifying and evaluating the risks your API faces. It can analyze the calls done to your API and notify you about any suspicious actors. You can also use a threat model to have a continuous cycle of improving your API by assessing its vulnerabilities and fixing them.
10. Consult Experts
If your business heavily relies on APIs, then it can be worth it to hire experts to train your cybersecurity team on the most common pitfalls of API development and how to avoid them. Alternatively, getting a consultation can significantly assist you with your understanding of API vulnerabilities.
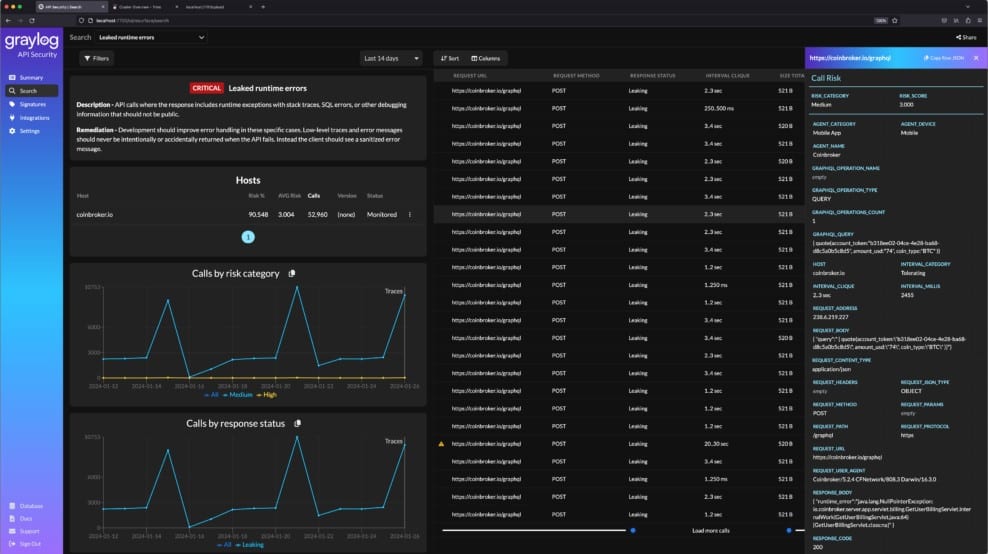
Graylog API Security – EDITOR’S CHOICE
Graylog API Security discovers and assesses all of the APIs that your applications call. You probably use APIs supplied by third-party software developers and you don’t have control over them. You probably can’t even access the code, so if the scanner in Graylog API Security discovers security weaknesses, you can’t fix them. However, the Graylog package provides an effective workaround.
The API search in Graylog API Security generates an inventory of software components to monitor. This discovery process repeats continuously, so any new APIs will be added to the list. The API Security service then scans each API for security errors. This process involves checking for well-known vulnerabilities, such as the OWASP Top 10. The package also runs the APIs with different inputs to actively test for security loopholes.
Key Features:
- Software component analysis: Generates an API inventory
- Vulnerability scanner: Looks for well-known security errors
- API testing: Runs APIs with different inputs to provoke any security weaknesses
- Bug fix reporting: Provides a prioritized list of security errors per API
- API bill of health: Confirms if an API has no security weaknesses
The vulnerability scanner will reveal security loopholes in the APIs embedded in your systems. Hackers can exploit those weaknesses to enter your system, cause havoc, damage data, or hijack your Web applications. So, you need to get those fixed. However, if you don’t own those APIs, you can only notify the supplier of the API and hope that they resolve those issues.
If you can’t survive without the insecure API, you will need to rely on the security monitoring service in the API Security package. This watches user activity and identifies sessions that are getting close to either discovering or exploiting those discovered weaknesses. If that happens, the system disconnects the session and blocks the source of the attempt.
Pros:
- Constant scanning: The vulnerability tester repeats continuously to confirm fixes or discover new weaknesses
- Vulnerability logging: Notifications of discovered weaknesses are written to the system console and to log files
- Activity records: The events in user sessions are logged
- Interface to SIEMs: Send logs to third-party security tools
- Automated responses: Get threats shut down without manual intervention
Cons:
- SaaS not offered: This is a software package and there is no SaaS option
Graylog API Security runs on the AWS, Azure, GCP, and IBM Cloud platforms. You can opt to download the software package and run it over the MicroK8s hypervisor, which installs on Windows, macOS, or Linux. Graylog offers a Free edition of API Security and this doubles up as a free trial for the more comprehensive paid edition.
EDITOR'S CHOICE
Graylog API Security is our top pick for an API Security system because it discovers all APIS and scans them for security weaknesses. It provides a list of bugs that need to be fixed, which you might not be able to do anything about because you don’t own the code. However, this package has a workaround that will protect the insecure API until a secure update is implemented. You have the option of running this package on your cloud account or you can download it onto your own site and host it yourself.
Download: 1 node and 16GB of local rolling storage FREE Access
Official Site: https://go2.graylog.org/api-security-free
OS: MicroK8s, AWS, Azure, GCP, or IBM Cloud
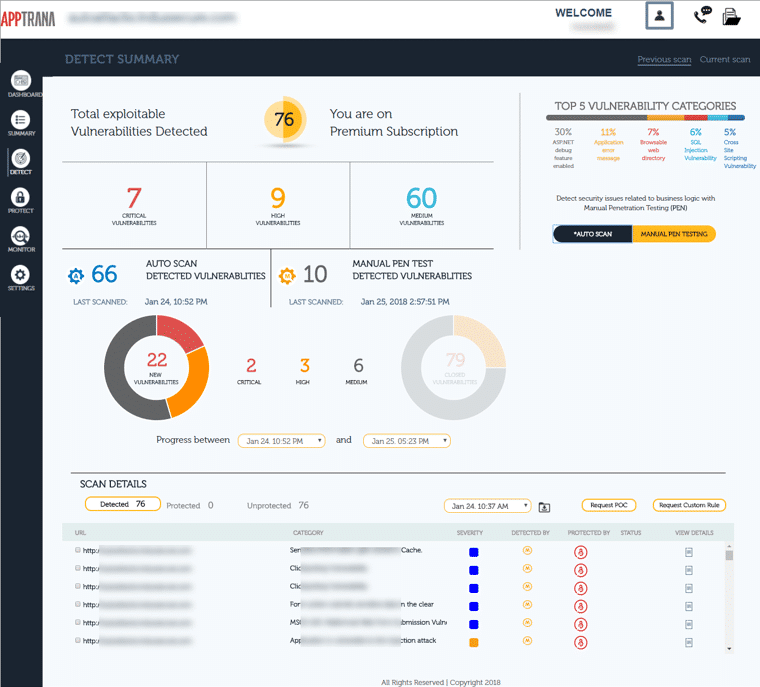
Indusface AppTrana
Another option to get expert input for your API protection is to get a managed security service. For example, Indusface AppTrana is a Web application firewall system for websites and API but the company also offers a SecOps team that will manage your Web assets using the platform. This team will implement API discovery and block malicious access attempts.
The team will also perform regular vulnerability scanning of your own Web systems and patch them where necessary. A pen testing tool will also check on your API security. Indusface offers AppTrana on a 14-day free trial.
11. Monitor Everything
If and when your API suffers an attack, you’ll want to be able to pull up audits and logs of every relevant occurrence on your server as quickly as possible. Therefore, you should get a tool that’s capable of recording this data. Keep the data for as long as you can internally; you continuously improve never know when a log history might turn out helpful in debugging.
12. Minimize Sharing
Have you ever thought about why many error messages are pretty unintuitive? “Something went wrong” doesn’t sound very informative after all. Companies make error messages like this so that malicious agents can get as little information under the hood from them as possible.
Maximum security requires you to be careful about sharing data. Because of this, you should use IP whitelists and blacklists to restrict which IPs can access your API.
To minimize human error, you’ll want to minimize how many admins the system has. Instead, split them into separate roles that don’t have access to information they aren’t likely to need.
13. Know The Bottom Line
Although APIs have become an ever-present element in modern app development (especially for mobile apps), an API will always be a greater security risk than a monolithic application. Therefore, you should also consider what API you’re using, as publicly available APIs rarely care much about their security.
Closing Words
These 13 steps are a great place to start with building up your API security. Although it can feel daunting at first, once you’ve worked with these measures in place for a bit, you’ll notice they don’t impede the development process much at all.
Sure, there’ll be a slight mixup where someone doesn’t have access to the data they need now and then, but that’s way better than suffering a data breach.
Once you’ve done these, our site has various other guides on how you can improve the security of any of your systems.
Does your company have a robust API security protocol?
What do you think about the trend of app development relying more and more on APIs?
Let us know in the comments below.