Auditing network security is a crucial element of any modern company. Auditing the IT assets and policies within your network can help you realize its weaknesses.
Furthermore, auditing gives a birds-eye view of your network that can be beneficial when you’re attempting to resolve a specific issue. Performing audits gives you a grasp of how well your enterprise is defended against common threats.
Today, we’ll be taking a look at the cream of the crop in network security auditing assets such as vulnerability and port scanners, patch managers, and a variety of other tools that can help your network security.
Here’s our list of the best network security auditing tools:
- SolarWinds Network Configuration Manager – FREE TRIAL Made by the reputable SolarWinds company, it combines an extensive list of features with a slick and intuitive GUI. Its customizability and smoothness give it the edge over the rest of its competition.
- ManageEngine Log360 – FREE TRIAL A SIEM service that includes Active Directory auditing and activity logging for compliance auditing in addition to its live activity alerting. Runs on Windows Server.
- ManageEngine ADAudit Plus – FREE TRIAL This package implements user behavior analysis, file integrity monitoring, Active Directory protection, and compliance auditing. Available for Windows Server, AWS, and Azure.
- SolarWinds RMM A subscription-based tool excellent for dealing with multiple sites at once.
- Intruder A cloud-based tool paid with a subscription model excellent for a buy it and leave it model of security auditing.
- Netwrix Auditor One of the best tools if you’re looking for a tool with excellent automation capabilities and a Rest API.
- Nessus A great template-based tool for beginners and advanced users alike.
- Nmap Nmap is an open-source tool with a lot of depth, offering customization if you want it, but still being quite good for beginner users.
- OpenVAS An open-source tool constantly updating its list of over 50,000 vulnerabilities.
The Best Network Security Auditing Tools
1. SolarWinds Network Configuration Manager – FREE TRIAL
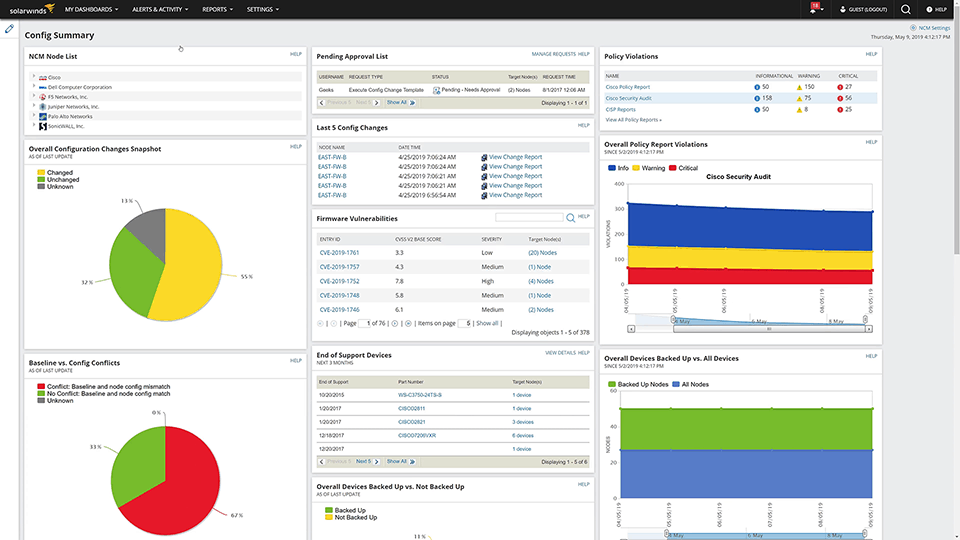
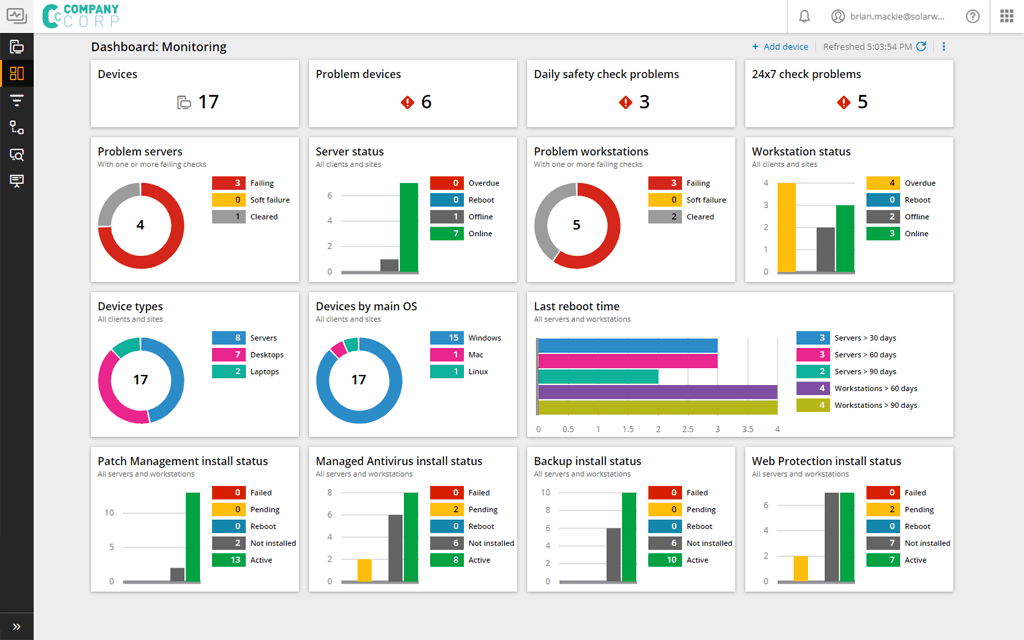
The SolarWinds Network Configuration Manager is an excellent tool for managing the configurations of your network devices. This device configuration & auditing tool allows you to deploy configurations to any device within your network, as well as take notice of unauthorized or incorrect configurations meddling with it.
Its network vulnerability scanner constantly tracks the whole network, and auto-updates any outdated devices. Its intuitive dashboard lets you take a look at a variety of different metrics and data to gain a good understanding of your network. It provides intuitive lists and graphs for metrics ranging from Overall Configuration Changes to Firmware Vulnerabilities.
There’s an abundance of other features such as alerts and reports. Its reporting ability allows you to create an audit report for the whole network or a specific device. The alerts feature notifies you whenever a configuration change takes place and gives you details on the changes made as well as the login ID that made them. If there’s an undesirable change, you’ll be able to roll back it as if it never happened.
The SolarWinds takes first place quite convincingly due to its ability to patch up vulnerabilities along your whole network. It’s available on Windows, and comes with a free 30-day trial, after which it will cost you upwards of $3,085 USD.
Download the 30-day FREE Trial
https://www.solarwinds.com/network-configuration-manager
2. ManageEngine Log360- FREE TRIAL
ManageEngine Log360 is a collection of security tools that is headlined by a SIEM service but also includes extensive activity logging and system auditing features. The entire package is able to operate on logs sourced from more than 700 applications and operating systems, which report in different log message formats.
The six tools included in the Log360 package include the EventLog Analyzer, which collects log messages, consolidated their different formats into a common format, stores them, and makes them available for analysis. Logs can be collected from cloud platforms as well as network endpoints.
The Log360 log management system files and archives log messages. This availability of logs stored in an orderly manner is an important requirement for compliance auditing. The package also includes a compliance reporting tool for HIPAA, PCI DSS, FISMA, SOX, GDPR, and GLBA.
Another system included in the Log360 bundle is ADAudit Plus, which assesses the objects and structures in Active Directory, highlighting weaknesses that need to be tightened. The tool logs all activity on the system, attributing the user account involved. This is a good assistant for identifying insider threats or account takeover events.
The SIEM provides live searches through arriving log messages and raises alerts when it discovers suspicious activities. Alerts can be channeled through service desk systems, including ManageEngine ServiceDesk Plus, Jira, and Kayoko.
ManageEngine Log360 runs on Windows Server and you can access the system with a 30-day free trial.
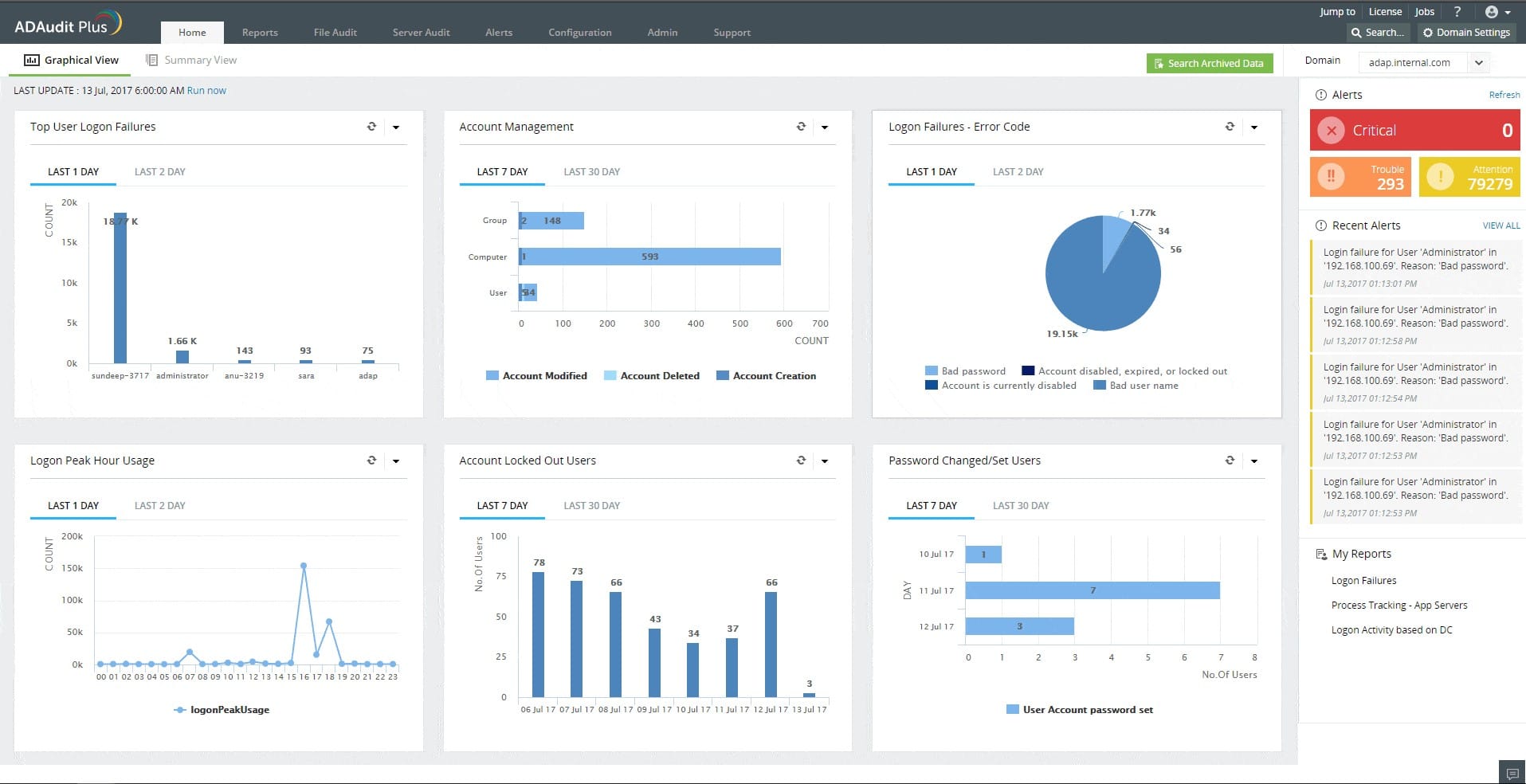
 3. ManageEngine ADAudit Plus – FREE TRIAL
3. ManageEngine ADAudit Plus – FREE TRIAL
ManageEngine ADAudit Plus is designed to audit file access activity and compile user behavior analysis. The logs that this tool creates are funneled through to a security auditing process.
There are three editions for this package and the lowest of these offers workstation activity monitoring and recording plus compliance auditing and reporting. The next edition up extends its monitoring and auditing services to servers.
The top plan provides activity logging and compliance auditing and also implements Active Directory protection. This service raises an alert if an objection AD is changed. Alerts appear in the system console but you can also set them up to be forwarded as notifications by email or SMS.
The auditing service in the tool is implemented by templates, which are a combination of search strings and layout formats. By running one of these reports you get a summary of the stored logs that record file access activity.
These audit reports also count as compliance reporting facilities. The auditing and reporting service can be tailored by specifying which data protection standard you need to follow. Options cater to SOX, HIPAA, PCI-DSS, FISMA, and GLBA.
ManageEngine ADAudit Plus is available for installation on Windows Server and you can also get it as a service on AWS or Azure. The workstation logging system forms the heart of the lowest edition, which is free to use. Two paid editions offer logging and auditing for servers (Standard) and logging for workstations and servers plus alerts on Active Directory changes (Professional). You can get the Professional edition on a 30-day free trial.
4. SolarWinds RMM
The SolarWinds RMM is based in the cloud and gives you access to a monitoring and risk management tool remotely. It’s also useful for giving you the ability to manage multiple sites at once.
Due to the fact many firms need the ability to keep track of their data usage for complying with data security standards, it’s great to have a tool that has data access tracking built in. The tool has auditing tools that will check whether you’re complying with standards like HIPAA or PCI-DSS.
The SolarWinds RMM also features PII (Personally identifiable information) exposure weakness assessments. The RMM’s usage analysis system lets data managers look at trends in data usage and determine data risk.
The RMM’s Risk Intelligence Module lets you find all PII as well as all tracks that have access to it. Having access to its ad hoc scans is very useful for any data security compliance auditor. This means things like detecting inappropriate permission discovery or reporting leaked/stolen data is a breeze.
This tool also has a variety of tools that help you protect your data from accidental loss such as its backup and restore functionalities.
The digital security capabilities of the RMM like endpoint detection and response helps secure any desktop devices. It’s also able to automatically keep your firmware and OS up to date. With all this, the RMM has an antivirus feature as well.
The SolarWinds RMM is subscription-based, however, you don’t need to pay any installation fees. There’s also a 30-day free trial available.
5. Intruder
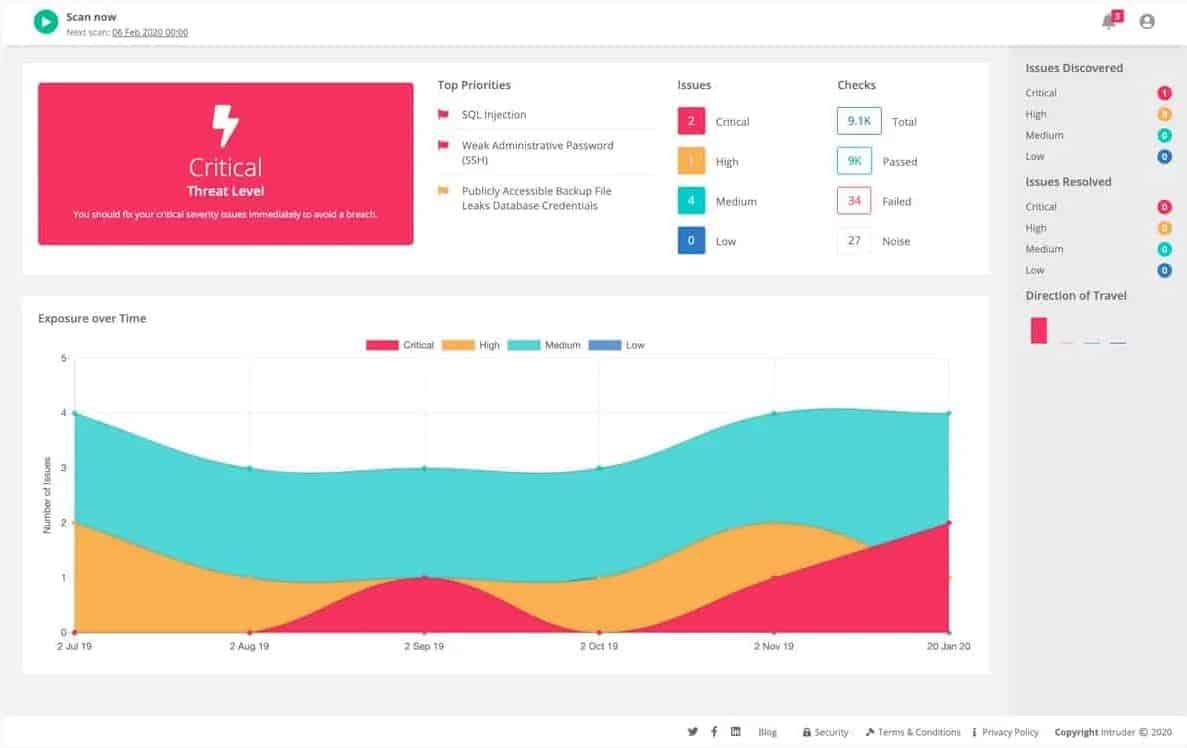
Intruder is a cloud-based vulnerability scanning tool. It’ll perform a detailed, monthly scan for every customer’s system, and will make an intermediate scan when a new threat appears in your service’s threat intelligence database.
When you sign up for this service and create your account, Intruder will launch a full scan of your whole system looking for vulnerabilities. It will then do this monthly, as well as in the event of an intruder getting an update to the threat intelligence database. In these cases, it’ll automatically scan customer systems, looking at the hardware and software vulnerable to the threat in great detail.
Due to being a cloud-based service, Intruder looks at your network from the same perspective as most malicious agents. Its scans look through every part of the IT infrastructure present on the customer site, as well as any cloud services being used by the client. Intruder looks for over 9000 vulnerabilities, ranging from basic ones like SQL injections to more specific ones.
If you choose to install an agent on your network, this tool can also look at whether your network is weak to insider threats.
Intruder has three different subscription models. They are:
- Essential: You get one monthly scan
- Pro: You get a monthly scan, as well as a facility to allow on-demand scanning
- Verified: This plan gives you everything the previous two do, plus the aid of a human team of penetration testers.
Furthermore, this tool offers a month-long free trial.
6. Netwrix Auditor
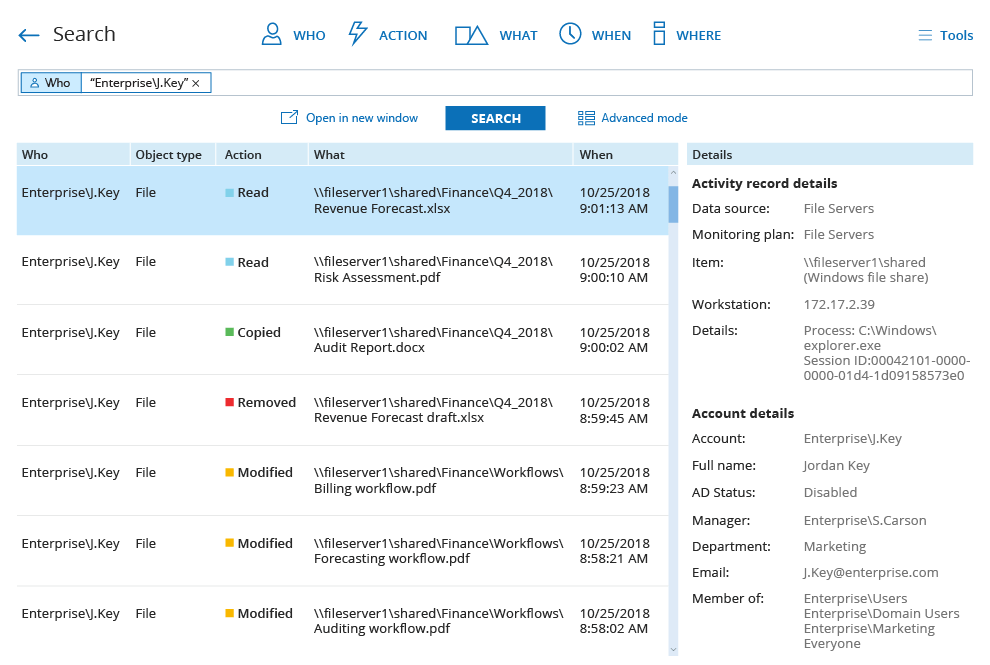
If you’re looking for a good tool to help you pay attention to configuration changes within your network, the Netwrix Auditor might just be the tool for you. You can see info on all system changes through its dashboard, such as Action, When, Where, Who, and What. This abundance of information is enough for you to understand the nature of the changes that happened.
Users can also see the info pertaining to login attempts, as well as any port scanning attempts. Failed logins are flagged with a red box, letting you spot attempts at breaking into your network at a moment’s notice. Furthermore, you can see all of the hardware monitoring info such as CPU temperature, or the status of your power supply or cooling fan.
The Netwrix also features an alerts system giving you automatic notifications for unusual events. You can also customize the scripts that the tool uses when an alert is made. You can use this to set up automatic Helpdesk tickets in case of specific events.
The Netwrix Auditor is one of the best tools for you if you’re looking for a tool with expansive automation capabilities and a rest API. Although its community edition is free, for a more in-depth look you’ll need to buy it. The price is determined based on a quote asked from the company directly, however, there is a 20-day free trial.
7. Nessus
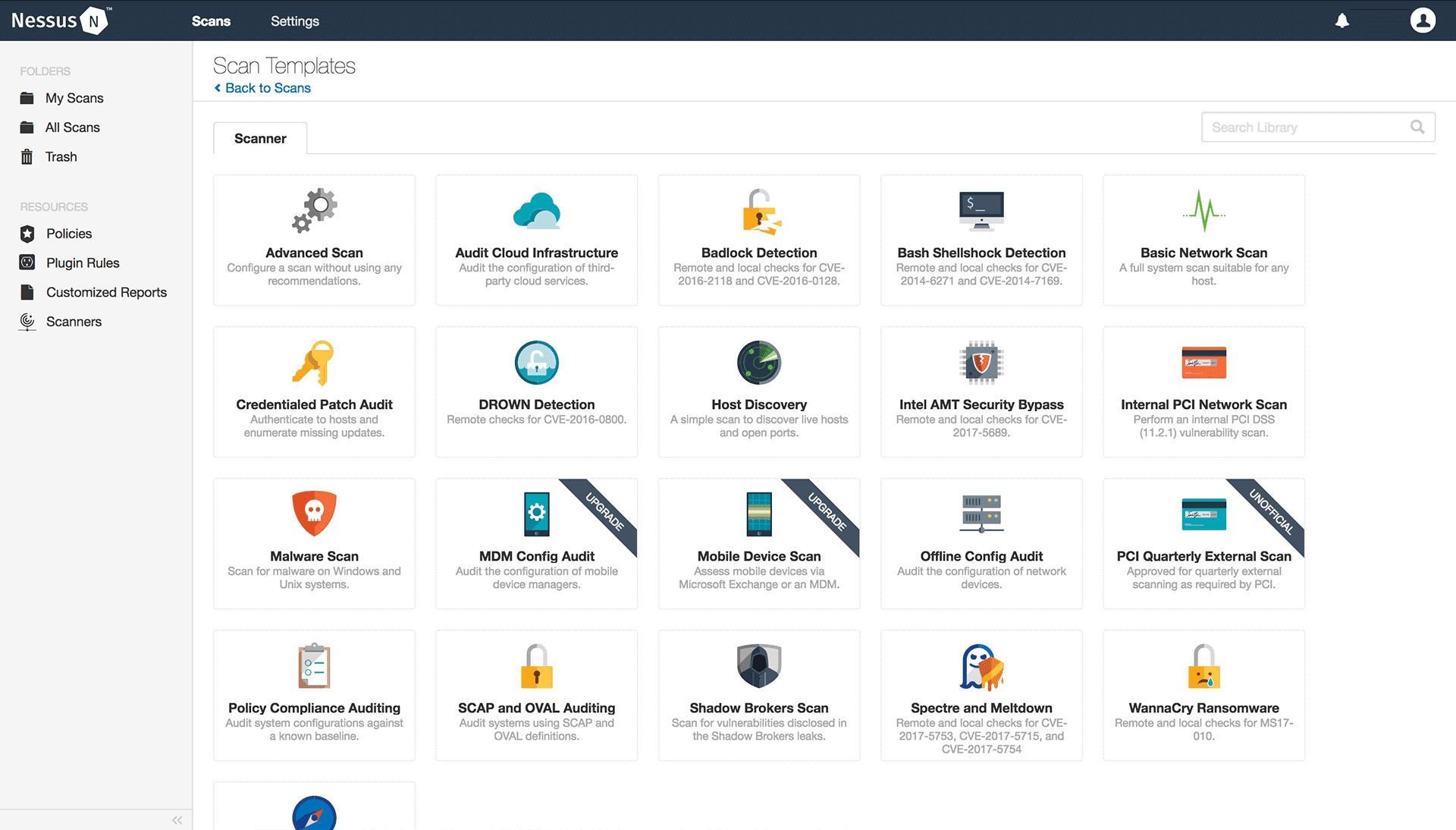
Nessus is an excellent tool if you’re looking for a tool to handle config and patch management as well as auditing for free. This tool is updated with new plugins made to respond to new threats around averaging once a day. These plugins are automatically installed so you’re always ready to intercept malicious activity.
Nessus configuration is quite simple, mostly due to its 450 default configuration templates. The versatility of these templates, such as Basic and Advanced network scans, Malware scans, and WannaCry Ransomware scans makes it very simple to find the weaknesses you’re looking for.
Nessus also supports custom report generation to help reflect new entry points. It lets you make reports going into detail on vulnerabilities within a host or plugin. An example of this is the tool letting you make a Hosts Executive Summary report that lets you see a host breakdown showing them as one of the following:
- Info
- Low
- Medium
- High
- Critical
These reports can also be shared with your team in CSV, .nessus XML, and HTML format.
If you’re looking for a tool that’s well-equipped for dealing with brand new online threats, its free (Essentials) edition supports up to 16 IPs. There is also a paid Nessus Professional edition costing $2,390 USD which comes with a free trial.
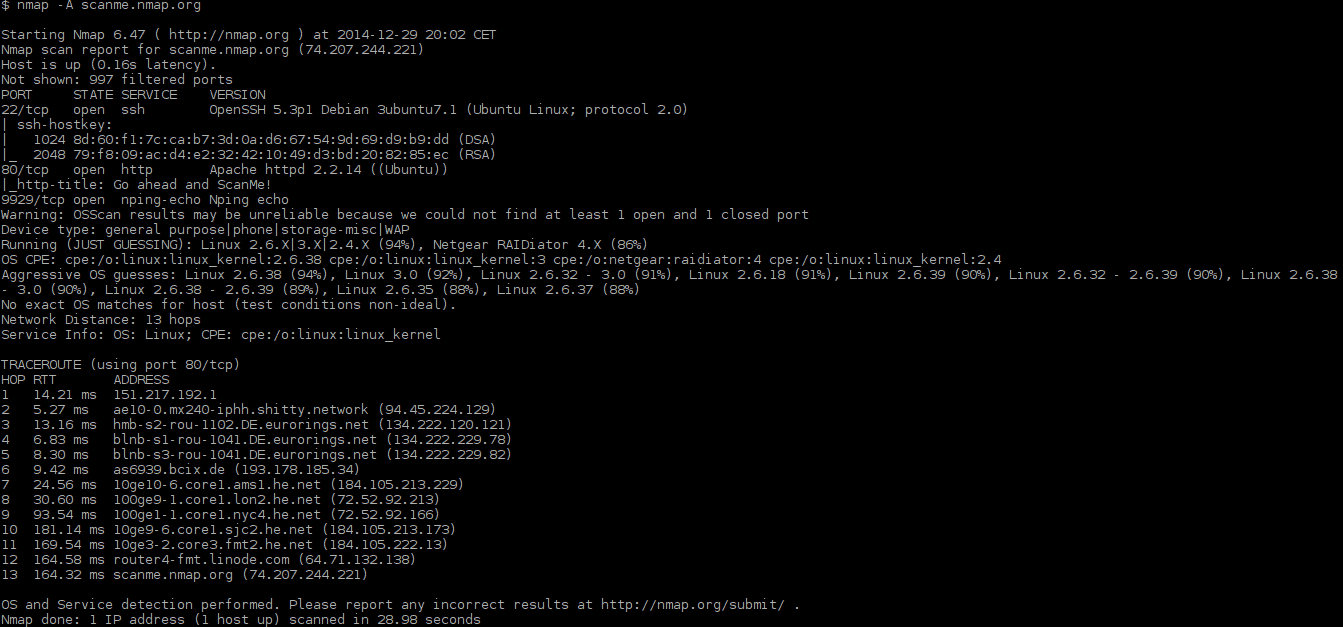
8. Nmap
Nmap is the first open-source tool on this list. It allows you to find hosts as well as vulnerable open ports. It’ll let you know the status of a chosen port through its command-line interface. You can also find more information on the entities found like their port, state, version, and service. Furthermore, you can find the OS version running software which can help you patch up obvious vulnerabilities.
Being open-source, Nmap, offers almost endless customizability, like its ability to do automatic scans by writing Lua scripts. Doing this can be a great asset as it can save the time it would take to run the scans manually.
There is also the option to create automated scans. Nmap allows you to write scripts in Lua to run scans automatically. Automating scans is beneficial because it saves you time so that you don’t have to run scans manually to discover vulnerabilities.
If you’d prefer to interact with the tool outside of a command-line interface, Nmap has a GUI version called Zenmap. It lets you save scan profiles, as well as run the most common scans without setting them up manually, they can also be saved for later analysis.
Nmap is an excellent port scanner due to its simplicity being great for new users, while still having an abundance of features for more advanced ones. It also runs on Windows, Linux, UNIX, and FreeBSD, in addition to being completely free of charge!
9. OpenVAS
Last but not least, we have OpenVAS, an open-source vulnerability scanner targeted towards Linux users, letting you do both authenticated and unauthenticated testing. The tool receives constant updates through the Greenbone Network Vulnerability Tests feed, giving it access to over 50,000 weaknesses.
It’s great for businesses that want an affordable yet effective vulnerability scanner. Being open-source, OpenVAS is completely free of charge.