Any network that grows past a few computers is too large to be monitored manually. Cyberattacks are becoming increasingly commonplace in today’s world, and businesses worldwide are losing millions to them. However, it’s not just large enterprises that are affected by this. SMBs face the threat of cyberattack just as much.
To protect yourself from cyberattacks, you might consider manually monitoring your network. However, as the business grows, this will become a more complex task, bordering on the impossible after just a dozen devices or so, and even before that, it’ll cost you a lot of work hours that could be better spent elsewhere.
Here is our list of the best network vulnerability scanners:
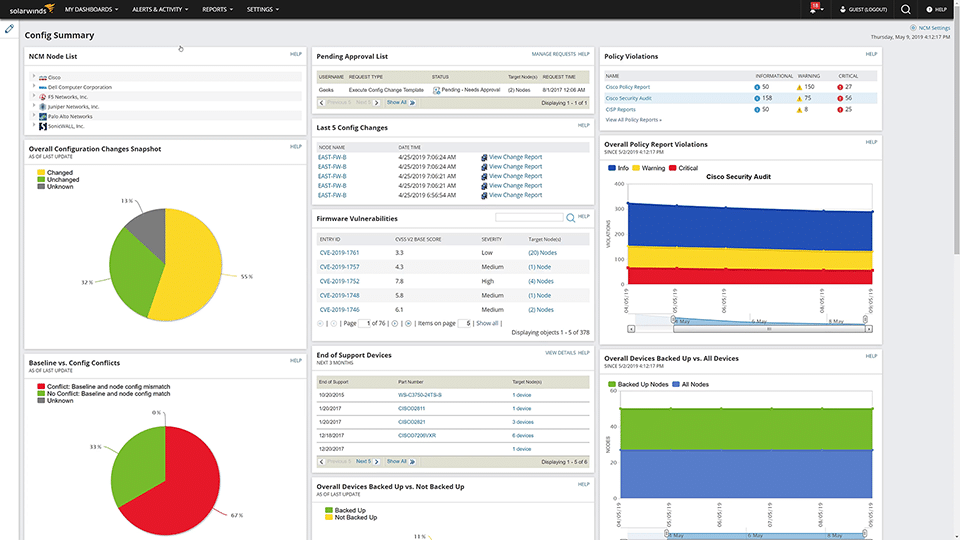
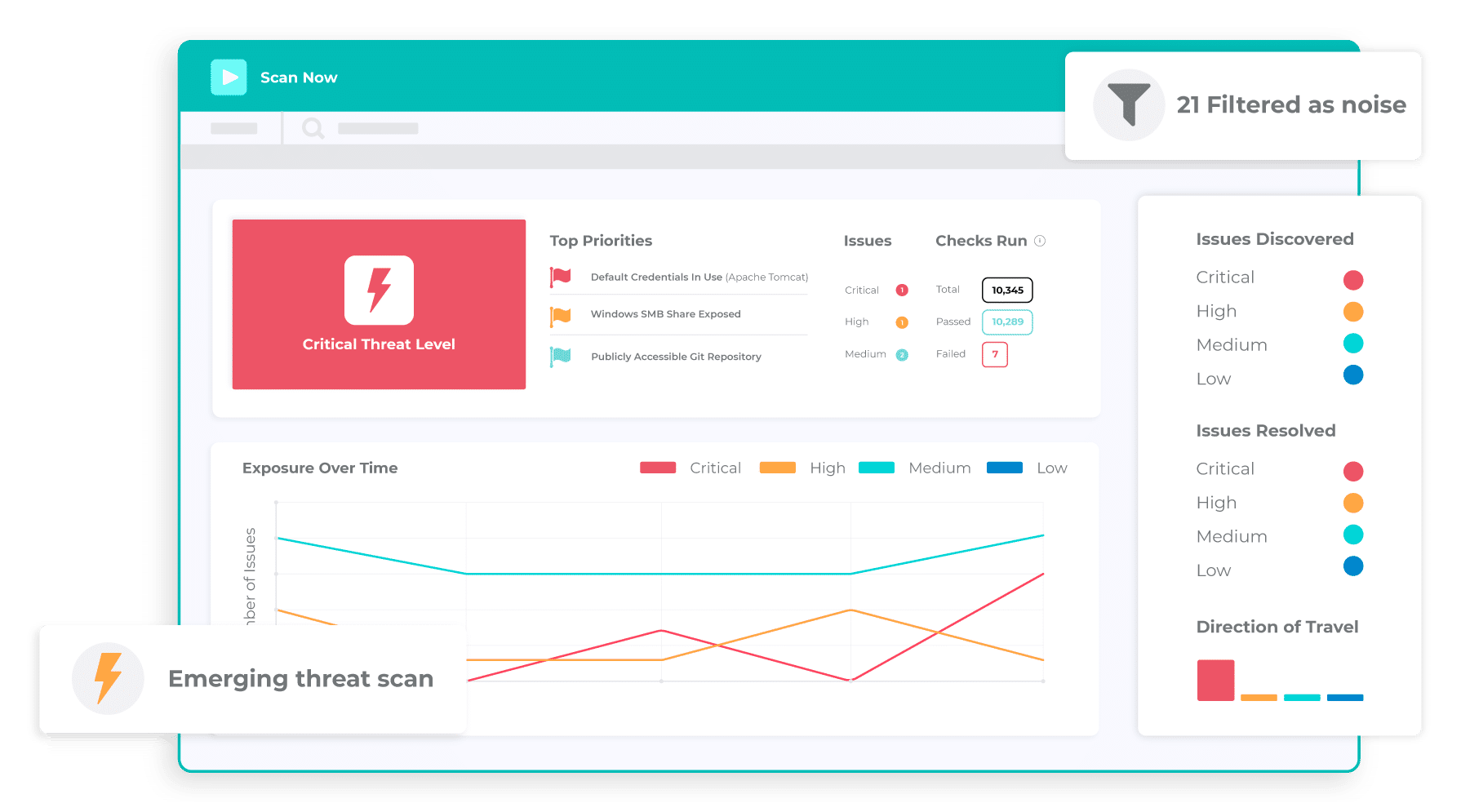
- SolarWinds Network Configuration Manager – FREE TRIAL The NCM comes with a vulnerability scanner and manager. With its autodiscovery features and highly detailed vulnerability scanning capabilities, it’s hard to go wrong with this tool. It’s one of the most scalable solutions out there and will quickly provide you with alerts and potential solutions whenever it finds an issue. Download a 30-day free trial.
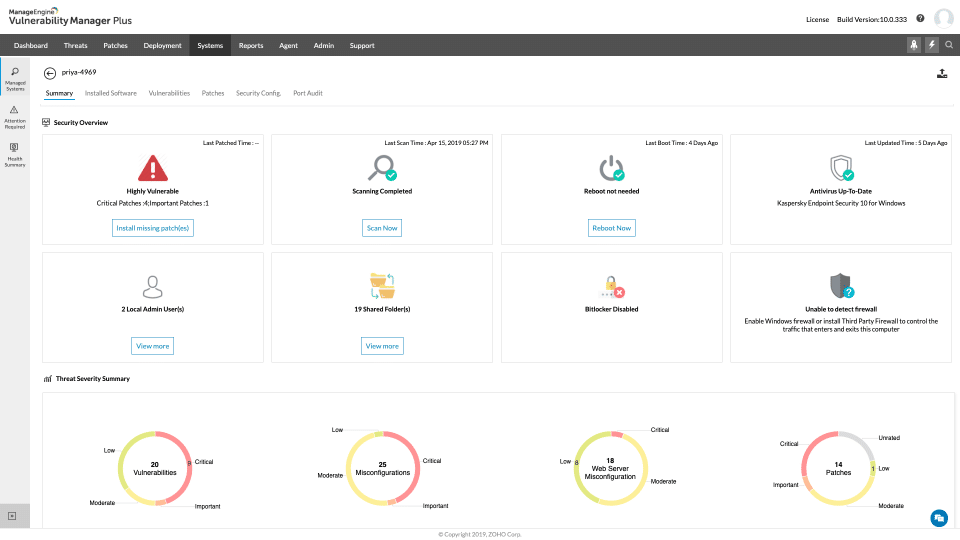
- ManageEngine Vulnerability Manager Plus – FREE TRIAL A tool with a configuration and patch manager bundled with it and an excellent free version. Download a 30-day free trial.
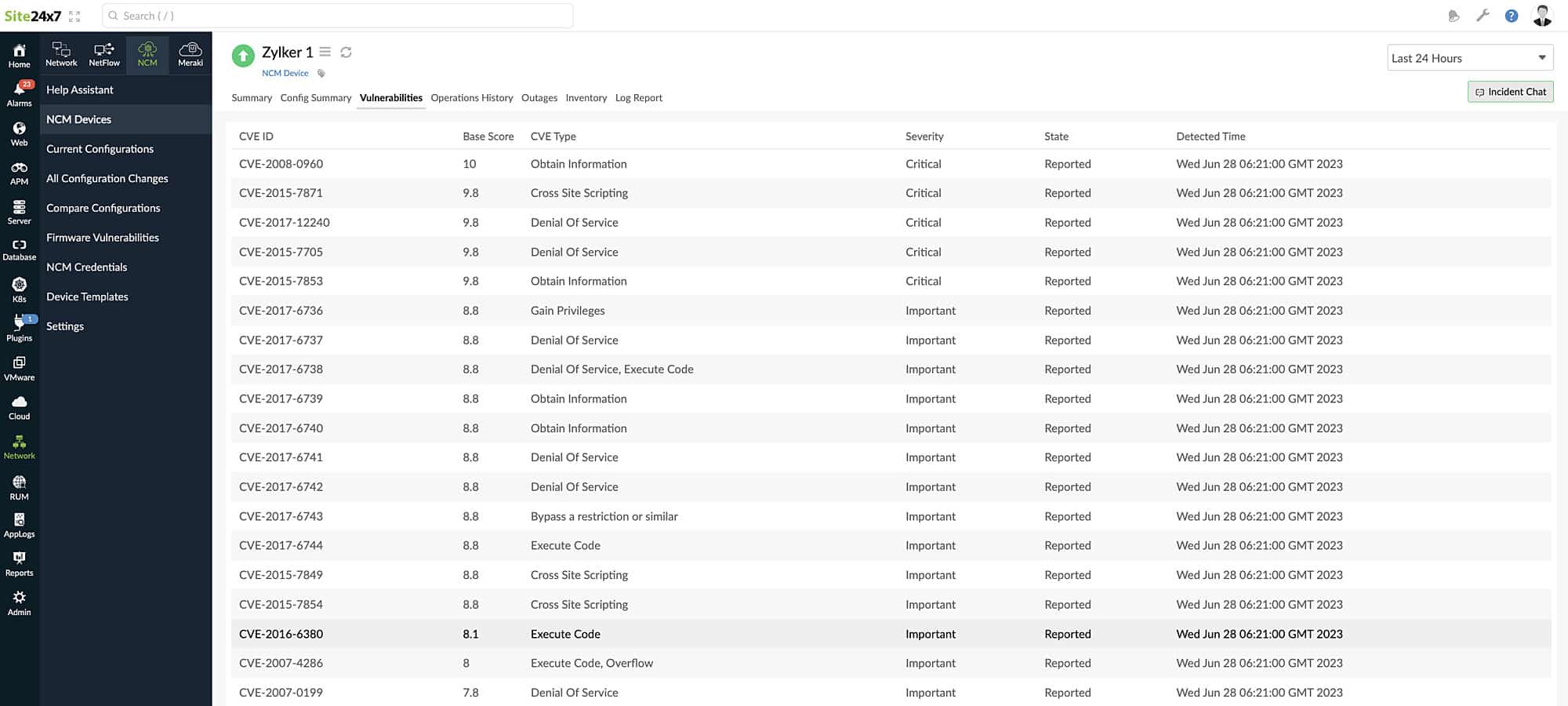
- Site24x7 – FREE TRIAL A vulnerability scanner that performs network scanning and vulnerability detection. It offers a range of features and a continuously updated vulnerability database. Start a 30-day free trial.
- CrowdStrike Falcon A cloud-based tool that integrates with the rest of the Falcon product line. It uses AI to bolster its performance significantly.
- Intruder Vulnerability Scanner A cloud-based tool that relies on its massive internal database boasts a modern, intuitive interface that could put most other tools to shame.
- Syxsense Secure A lightweight tool that supports various automated features to make your life easier.
- Paessler PRTG A sensor-based tool that offers unparalleled depth and lets you pick and choose which features you want to use and pay for.
- SecPod SanerNow Vulnerability Management A tool that comes with a patch and asset manager and is great at ensuring compliance to data security standards.
Today, we’ll be looking at some of the best network vulnerability scanners to ensure that this isn’t an issue you’ll have to face again.
The Best Network Vulnerability Scanners
1. SolarWinds Network Configuration Manager – FREE TRIAL
The SolarWinds Network Configuration Manager or NCM is a vulnerability scanner, and a management tool for vulnerabilities originating from the router or switch misconfigurations. This tool focuses on remediating issues, ensuring you’re complying with security audits, and monitoring your network for unexpected alterations.
Key Features
- Extremely detailed vulnerability scanning
- Provides steps you can take to correct any issues it finds
- Automatic detection of config changes
- Audits routers and switches for compliance with a variety of security protocols
- Excellent, customizable UI and alerts system
- You can set up automatic updates to hundreds of devices at once
- Extremely scalable
If it detects a vulnerability caused by a configuration error, it can run one of its many remediation scripts to resolve the situation or deploy an update to hundreds of devices at once. If an unauthorized change is detected, it will let you roll back before it occurred with a single press of a button.
To help with malicious changes or regressions, it gives you access to config change monitoring and couples this with its customizable alerts system. It will also continuously audit your switches and routers to ensure DISA, FISMA, STIG, and NIST compliance at all times.
With that being said, the SolarWinds Network Configuration Manager was made for businesses that have network technicians. Unfortunately, this means that home users or SMBs without a technically-inclined individual among them will have trouble using it.
The SolarWinds Network Configuration Manager comes with a 30-day free trial.
2. ManageEngine Vulnerability Manager Plus – FREE TRIAL
ManageEngine makes various IT infrastructure management and network monitoring tools, with ManageEngine Vulnerability Manager Plus coming as their entry in the system protection field. The tool mainly focuses on catering to enterprises; however, there’s a free version suitable for some SMBs and protects up to 25 different devices.
Key Features
- Has a configuration and patch manager bundled with it
- The free version offers a lot of valuable functionalities
- Many powerful options like Wake-on-LAN and remote shutdowns can be triggered from its dashboard. You can also set them up as automatic mitigation processes
- A variety of reporting features can help you track how well it’s performing
- Excellent for supporting large enterprises
- Runs on Linux, macOS, and Windows
In the free version, you’ll have access to both its on-demand and scheduled vulnerability scans to find problems within your network. In addition, it uses a highly advanced scanner to find zero-day vulnerabilities, performing significantly better than database-driven detection.
The most significant vulnerabilities are often found within weak configurations and out-of-date software or firmware. The Manager Plus has a configuration and patch manager to stop these weaknesses from affecting your business. If the vulnerability scanner finds issues that patches and updates can fix, the patch manager will automatically roll these out; however, you can customize this so that some software isn’t updated if you don’t want it to be.
System admins gain access to various unique tools within the dashboard that let them get more out of the software. For example, you can integrate Active Directory authentication, tailor the utilities on the dashboard, and much more.
Like most enterprise-level software, the ManageEngine is complicated to learn for beginners and non-technical users. However, if the free version doesn’t meet your standards, you can get a 30-day free trial of its two paid versions.
3. Site24x7 Network Vulnerability Scanner – FREE TRIAL
Site24x7 is a popular monitoring tool for networks as it helps scan top risks and vulnerabilities in real-time. It comes with a Network Configuration Management (NCM) feature and firmware vulnerability scanner that helps organizations gain clear visibility into the risks and their severity level.
Key Features
- Track unauthorized access and breaches
- Vulnerability Scanning
- Prioritize patch fixes
- Maintains compliance
Why do we recommend it?
Site24x7 comes with a wide range of features including NCM that help enterprises in securely and effectively manage network devices. The Site24x7 Firmware Vulnerability Management solution further aids in assisting network configuration and change management while ensuring compliance.
Firmware vulnerabilities result in device malfunctioning, privacy breaches, and other risks that can impact your network performance. However, with Site24x7 Firmware Vulnerability Management solution, you can secure your network and prevent such vulnerabilities from affecting your network devices. Further, it helps users learn about unauthorized access or disruption caused due to firmware vulnerabilities and secure the networks.
Additionally, with the help of this tool, you can monitor the list of vulnerable devices, check the exposed ones, record firmware versions, and review comprehensive details regarding every vulnerability.
Who is it recommended for?
Any company, be it small or large, that wants to monitor its network performance, scan firmware vulnerabilities in real-time, and cut down on downtime, including network administrators, can purchase Site24x7. However, large businesses that require greater capacity must pay an additional cost.
Pros:
- Helps reduce vulnerabilities with the distribution of firmware updates
- Helps run regular scans and categorize risk based on severity level
- Protects devices by maintaining the latest security patches and updates
- Maintains compliance while addressing configuration and change management issues
Cons:
- Would be nice to have a longer trial period for this tool
Site24x7 offers a 30-day free trial.
4. CrowdStrike Falcon
CrowdStrike Falcon is a cloud-based endpoint protection software. It’ll cover your entire network by defending its boundaries, in addition to investigating all of the activity that occurs on it, looking for suspicious activity. This tool comprises a variety of modules, each of which does a specific task such as hunting for threats or identifying malware.
Key Features
- Integration with other Falcon products
- Cloud-based service with an on-site agent
- AI services that enhance the tool’s performance
- Excellent alerts system
- Site-neutral, you can deploy Falcon Spotlight regardless of how many sites you want to be monitored
The vulnerability management module of the CrowdStrike Falcon software is Falcon Spotlight. Although it is a standalone product, it works best when paired up with other products within the Falcon line.
The Falcon Spotlight utilizes a mix of AI detection and its threat intelligence database to find vulnerabilities. The database is, much like Intruder’s, updated every time a threat is found.
It’s notable that although Spotlight is a cloud-based system, it still requires an on-site agent. With that being said, having an agent has some upsides as well; for example, you won’t have trouble managing vulnerabilities in case your internet connection goes down.
With that being said, the tool only offers a 15-day free trial, and its threat database is a bit lacking compared to the Intruder.
5. Intruder Vulnerability Scanner
The Intruder Vulnerability Scanner is a cloud-based SaaS tool that provides you with three levels of vulnerability scanning. Its basic level contains a monthly scan of your system wherein it will look for vulnerabilities in your system. This is supported by its massive central database of the most common attack vectors, updated whenever one is found.
Key Features
- Incredibly slick UI with an amazingly responsive interface
- Scheduled vulnerability scans, with additional scans whenever a new attack vector is found
- Cloud-based solution
- Finds vulnerabilities within web apps, databases, operating systems, and cloud services
- Multiple payment levels make it customizable for businesses of all sizes
- Very intuitive for such a high-level tool
Most vulnerabilities have already been exploited for an attack at some point, meaning this tool will help you avoid the mistakes other companies have made. Additionally, all devices using Intruder Vulnerability Scanner get an automatic scan whenever a new attack vector is found.
The second level is called Pro and offers an on-demand scanning utility. Finally, the third level- Verified, letting you take advantage of human pen testers. All plans are billed on either a monthly or a cheaper annual basis.
The two higher levels also look at your on-prem resources and all of the cloud services you use. Furthermore, as it’s a cloud service, Intruder is available from any web browser.
The Intruder’s biggest downside is that only the higher two levels get on-demand scans, and it can take quite a while to familiarize yourself with some of its more advanced features.
There’s a 14-day free trial available for the Intruder Vulnerability Scanner.
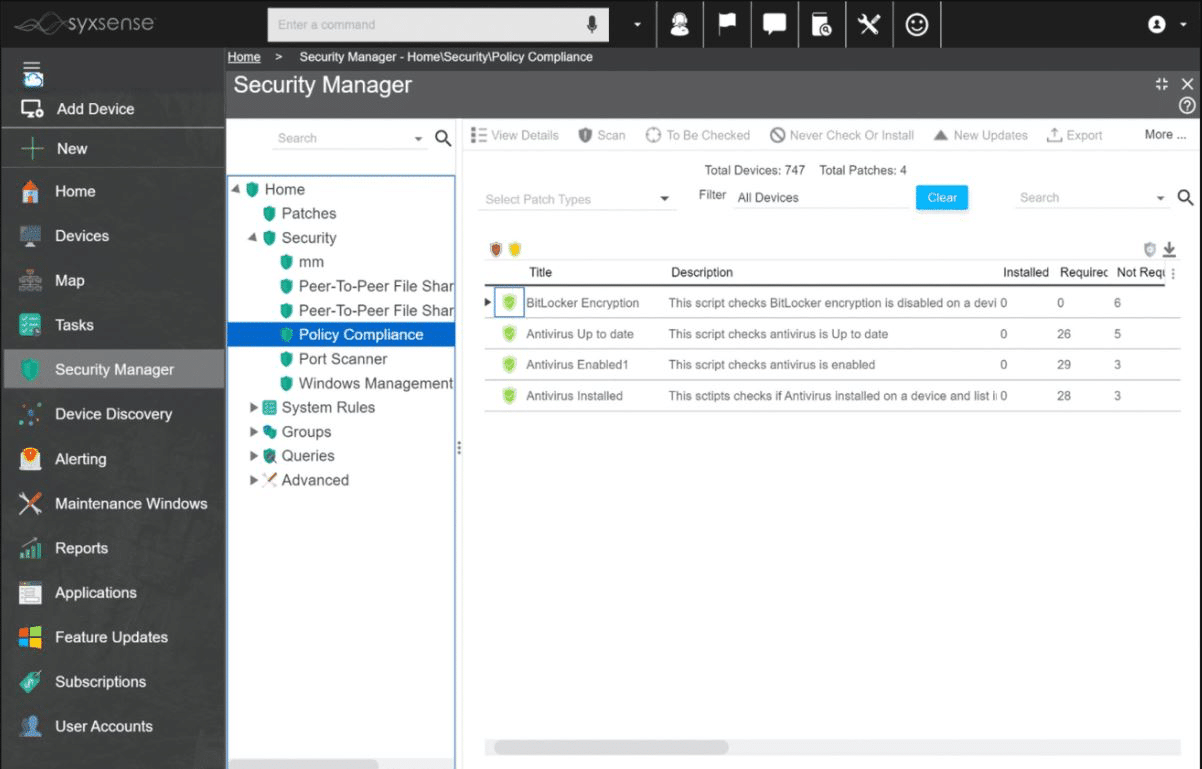
6. Syxsense Secure
This is yet another endpoint security software that uses its vulnerability scanner as its core. Syxsense has various automated features that will help you manage your network, and this functionality sets it apart from other vulnerability scanners.
Key Features
- Automatic remediation through the use of automated scripts
- Syxsense supports Linux, macOS, and Windows
- Automatically discovers all devices on the network and creates a network topology map
- Very lightweight
When you start Syxsense, its package will scan your entire network to find the endpoints within, even those on IoT devices. From there, it’ll create an asset inventory and create a network topology map for you to use. This process is constantly running, so whenever you change your network, it’ll immediately recognize it and alter the map accordingly.
If a vulnerability scan comes up positive, the tool will immediately start a remediation process alongside a patch manager that will help you quickly secure all endpoints. Although every device needs to have a Syxsense agent installed, you can control Syxsense through the cloud.
You’ll be able to remotely access each device guarded with Syxsense, and the tool also has a Wake-on-LAN feature. In addition, the tool’s logging functionalities make it great for complying with standard protocols like PCI, DSS, HIPAA, and the like. These audit logs are kept on their servers and won’t get deleted until their total size reaches 100GB.
One of the best things about Syxsense is how versatile it is. Whether you want to start remediation immediately, quarantine a threat, or simply update your systems, it can help you facilitate it and likely automate parts of the process.
With that being said, the tool can be a bit cumbersome to use until you get to grips with it. Syxsense is priced on a subscription model, with the cheapest option monitoring up to 10 devices for $960 per year. There’s also a 14-day free trial if you’d like to give it a shot before committing to a purchase.
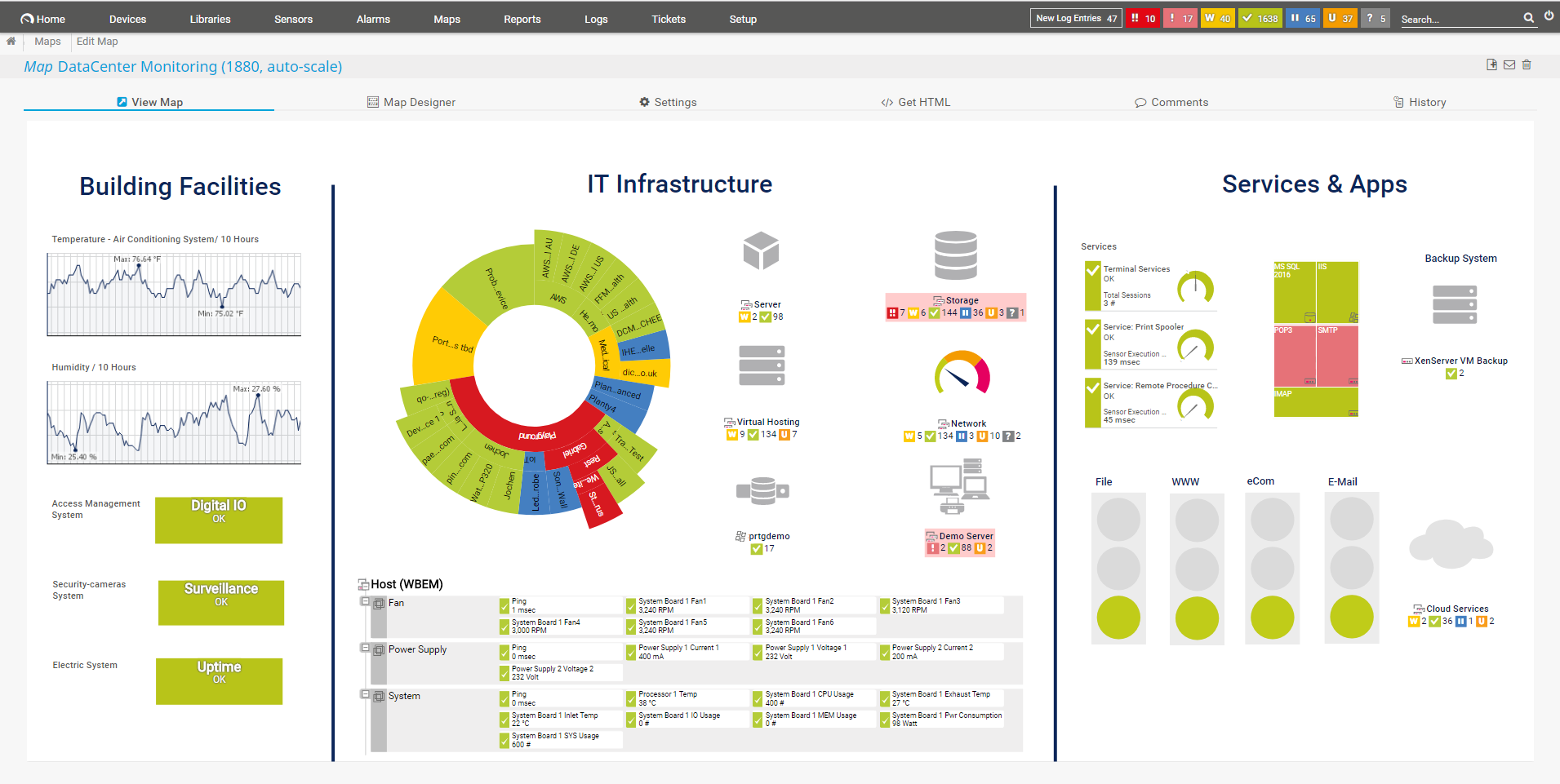
7. Paessler PRTG
PRTG is a system monitoring software developed by Paessler. It’s a holistic infrastructure monitoring software that will take care of your network, as well as the servers and applications within it. The PRTG is essentially a bundle of many sensors that do a specific task. It’s also priced on a per-sensor basis, letting you pay only for the features you want to have.
Key Features
- PRTG is free for up to 100 sensors
- Excellent for businesses that are looking to use one tool for all their monitoring needs
- Finds malicious activity and alerts you proactively
- Very scalable
- Automatically detects the devices on your network and creates an inventory
PRTG will automatically discover all of the devices on your network. If you change devices, the change will be automatically detected. The PRTG then monitors each of these devices and looks at status changes and alert conditions. Its network traffic monitoring capabilities can also show you unusual activity that might signal a malicious agent has entered your network.
It also contains a packet sniffing sensor that you can use to attain deep packet inspection, which will show you data on the specific protocols within your traffic. You can sort these by their source, destination, port number, or various other identifiers.
By far, the most significant benefit of the PRTG is that you can pick and choose which sensors you want to use. This can let you customize your vulnerability monitoring experience as much as you’d like. However, the dashboard is surprisingly easy to look at and gather insights from despite all this versatility.
All that being said, PRTG’s customization doesn’t come without a cost. It’s one of the most challenging tools to use to its fullest potential; however, a quality IT technician can work wonders with it. Furthermore, there’s a 30-day free trial where you can try it out with as many sensors as you’d like while still getting all of the security patches, system updates, and even customer support it offers.
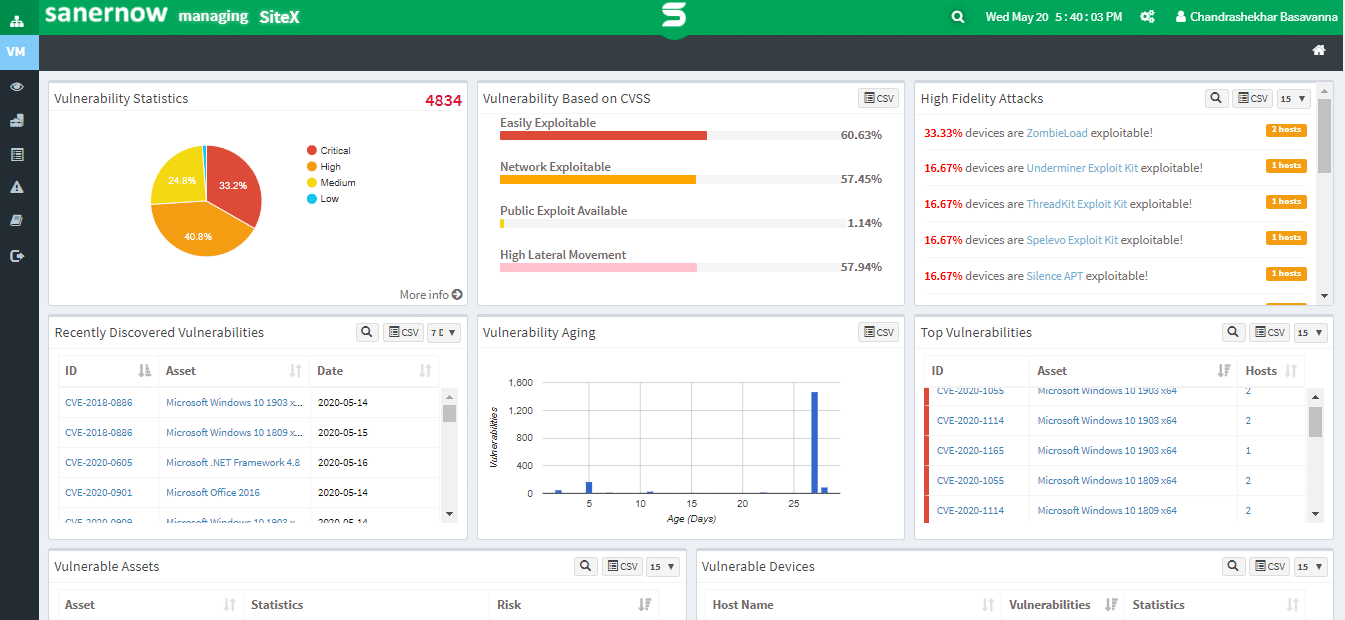
8. SecPod SanerNow Vulnerability Management
SecPod SanerNow Vulnerability Management is a cyber-hygiene software with security management functionalities. The tool is cloud-based and allows you to scan your network, find and assess threats, as well as prioritize and remediate them as you see fit, all from the same console window.
Key Features
- Comes together with a patch and asset manager
- Suitable for ensuring data privacy standard compliance
- All of the functions the tool performs are automatically logged
- You can pick how often SecPod scans your network
- Works on Linux, macOS, and Windows
This is yet another set of tools that relies on its vulnerability scanning functionalities to perform most of its magic. The tool periodically scans the endpoints within your network and ensures you’re complying with PCI, DSS, GDPR, or HIPAA standards.
This tool looks at each device individually and all of the ports and settings of its OS. It’ll look at the patch status of the device by looking at the OS version and suggest updates if necessary.
You can set up the exact frequency the tool will scan your network. It can go as low as once every 5 minutes. The scanner looks for vulnerabilities within the SCAP, or Security Content Automation Protocol database, which currently contains more than 130,000 factors.
Its remediation process is implemented through its patch manager. Once it finds vulnerabilities, it will attempt to access the sites of each software or OS vendor and request patches or updates. The patch manager then applies these patches to all devices that need them.
With that being said, the tool lacks features compared to other multitools, and its database isn’t quite as large as some of the other tools. However, the tool is priced on a per-quote basis, and you can get a free, 30-day trial today.
Closing Words
Picking the best network vulnerability scanner for your network is never easy. Unfortunately, there’s no list out there that can replace your judgment. After all, the most important thing about picking out any tool is having a realistic outlook on your needs. This means looking at the size of your network, the OSs operating on your devices, what features you need the most, how much you’re willing to spend in terms of funding, and a variety of other factors.
If you’re an SMB looking to start with a free solution geared towards enterprises so you can learn it for the future, then our 7th place might fare better than the 1st. On the other hand, if you’re only looking for a select few functionalities, then the Paessler PRTG might be the best.
With that being said, we’ve done our best to ensure that the top few spots are taken by tools that you can pretty much never go wrong with, as they offer a significant amount of functionality combined with intuitive user interfaces.
What are your favorite network vulnerability scanners?
What feature have you seen that you wish more tools would incorporate?
Let us know in the comments below!